window.open(url, name) is vulnerable to XSS with name collision · Issue #262 · w3c/html · GitHub
Por um escritor misterioso
Last updated 10 novembro 2024
Xiaoran Wang (xiaoran@attacker-domain.com) This is a joint research with Travis Safford. window.open(url, name, [args]) makes it easy for websites accepting user supplied URLs to be vulnerable when attackers can cause a collision on the
window.open(url, name) is vulnerable to XSS with name collision · Issue # 262 · w3c/html · GitHub

writeups/bug.md at main · tess-ss/writeups · GitHub

Automating Discovery and Exploiting DOM (Client) XSS Vulnerabilities using Sboxr — Part 3, by Riyaz Walikar
Missing required argument $name · Issue #294 · Smile-SA/elasticsuite · GitHub
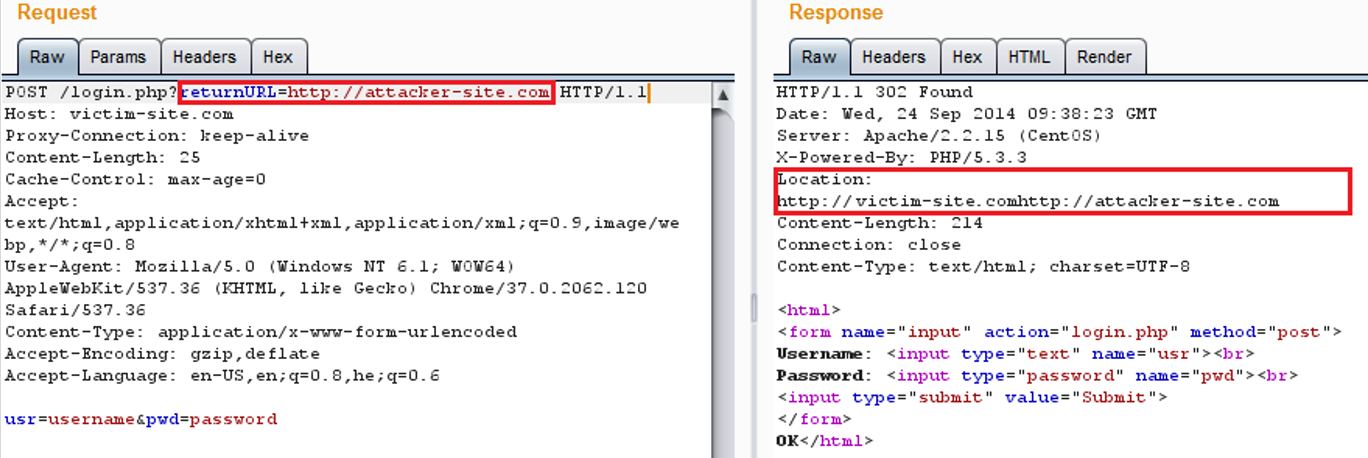
AppSec-Labs, Application Security

reactjs - WebStorm unable to recognise Next.js project - Stack Overflow
GitHub - payloadbox/xss-payload-list: 🎯 Cross Site Scripting ( XSS ) Vulnerability Payload List

certificate - React Native Facebook Flipper Thread 9: EXC_BAD_ACCESS (code=1, address=0x201) - Stack Overflow

Cross-site scripting (Practice on PortSwigger) - HackMD

Security Weekly Podcast Network (Video)

eclipse - The type org.openqa.selenium.chrome.ChromeDriver is not accessible - Stack Overflow

java - Invalid port. Exiting..Exception in thread main org.openqa.selenium.WebDriverException: Driver server process died prematurely ChromeDriver Selenium - Stack Overflow
Recomendado para você
-
 xsss – Tio Arthur10 novembro 2024
xsss – Tio Arthur10 novembro 2024 -
 Defending Node Applications from SQL Injection, XSS, & CSRF10 novembro 2024
Defending Node Applications from SQL Injection, XSS, & CSRF10 novembro 2024 -
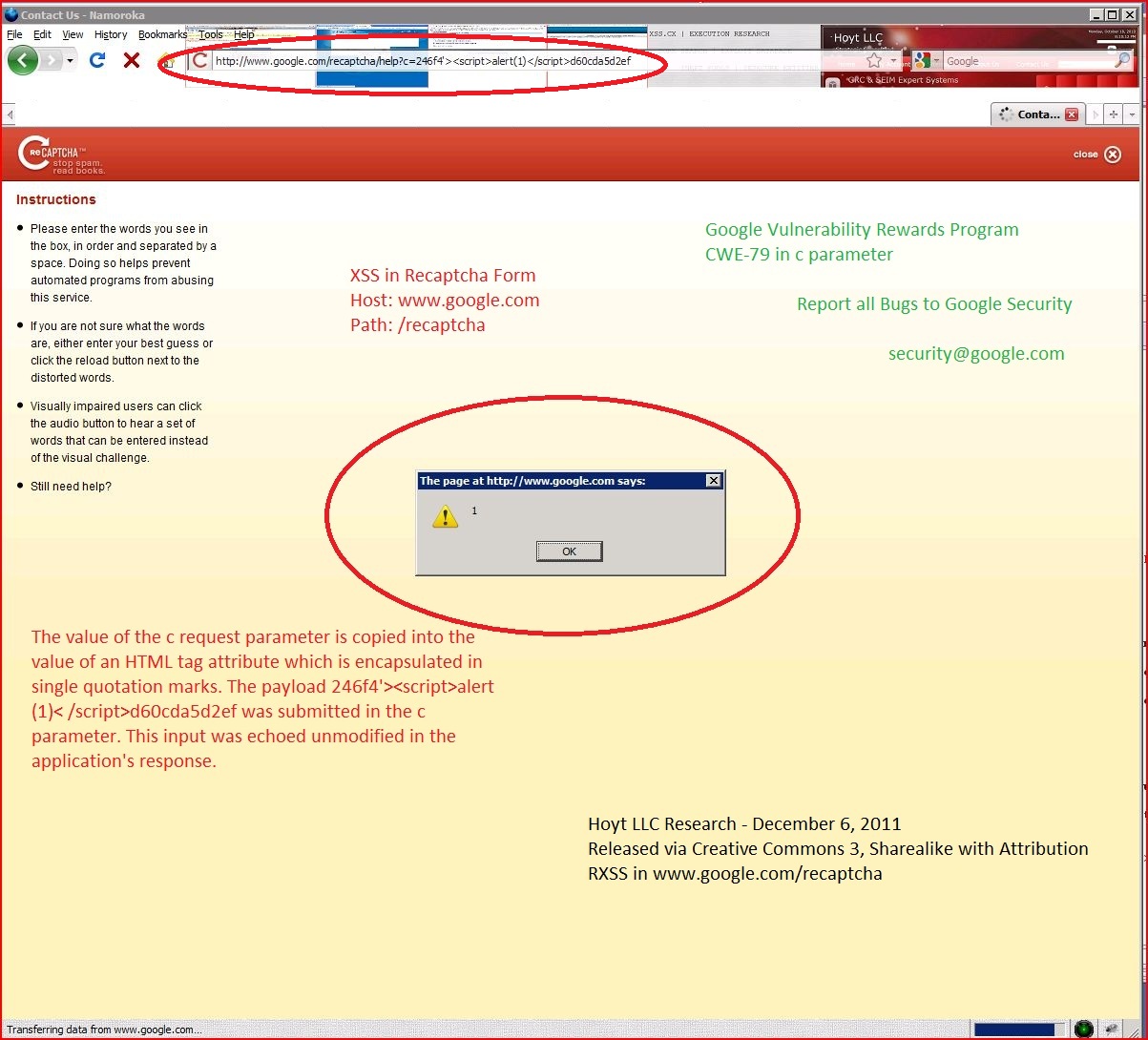 Google Vulnerability Rewards Program, XSS, Best Practices10 novembro 2024
Google Vulnerability Rewards Program, XSS, Best Practices10 novembro 2024 -
 Perfume Black Xsss De Paco Rabanne Masculino Eau de Toilette10 novembro 2024
Perfume Black Xsss De Paco Rabanne Masculino Eau de Toilette10 novembro 2024 -
 XSStrike misses XSS if server redirects because of lack of cookies10 novembro 2024
XSStrike misses XSS if server redirects because of lack of cookies10 novembro 2024 -
bhattidab_yt Subscribe to my channel please the link is in my bio10 novembro 2024
-
 Two examples of Algorithm 2 executions that find the MFSs and XSSs10 novembro 2024
Two examples of Algorithm 2 executions that find the MFSs and XSSs10 novembro 2024 -
 XSSS-ZC Transparent Rain Cloth, Rain Tarpaulin, PVC Windshield Cloth, Balcony Plastic Cloth, Canvas, Oil Cloth,4m*8m10 novembro 2024
XSSS-ZC Transparent Rain Cloth, Rain Tarpaulin, PVC Windshield Cloth, Balcony Plastic Cloth, Canvas, Oil Cloth,4m*8m10 novembro 2024 -
 XSSS-ZC Transparent Rain Cloth, Rain Tarpaulin, PVC Windshield Cloth, Balcony Plastic Cloth, Canvas, Oil Cloth,4m*10m10 novembro 2024
XSSS-ZC Transparent Rain Cloth, Rain Tarpaulin, PVC Windshield Cloth, Balcony Plastic Cloth, Canvas, Oil Cloth,4m*10m10 novembro 2024 -
OWASP Top 10 for JavaScript — A2: Cross Site Scripting — XSS, by Bekk Consulting10 novembro 2024
você pode gostar
-
 CORRE!! 🤯 MELHOR EXECUTOR MOBILE ATUALIZADO e SCRIPT BLOX PARA CELULAR E PC UPDATE 20!AUTO LEVIATHAN10 novembro 2024
CORRE!! 🤯 MELHOR EXECUTOR MOBILE ATUALIZADO e SCRIPT BLOX PARA CELULAR E PC UPDATE 20!AUTO LEVIATHAN10 novembro 2024 -
 Lords Mobile - Review10 novembro 2024
Lords Mobile - Review10 novembro 2024 -
 Old Potters Low Fire Pottery Clay (Cones 06-02) Art Modeling Clay, Ideal for Wheel Throwing and Hand Building, Pottery Clay for Sculpting, Beginners10 novembro 2024
Old Potters Low Fire Pottery Clay (Cones 06-02) Art Modeling Clay, Ideal for Wheel Throwing and Hand Building, Pottery Clay for Sculpting, Beginners10 novembro 2024 -
 Tell Me About a Time You Made a Mistake (Examples) – Career Sidekick10 novembro 2024
Tell Me About a Time You Made a Mistake (Examples) – Career Sidekick10 novembro 2024 -
 As vantagens e desvantagens do videogame para a saúde10 novembro 2024
As vantagens e desvantagens do videogame para a saúde10 novembro 2024 -
 Desenho Nightmare Five Nights at Freddy's, fnaf 5 bon bon, png10 novembro 2024
Desenho Nightmare Five Nights at Freddy's, fnaf 5 bon bon, png10 novembro 2024 -
 Bola basquete Penalty pro IV 3x3 - unissex - vermelho+bege, Penalty, Bolas, VRM/BGE10 novembro 2024
Bola basquete Penalty pro IV 3x3 - unissex - vermelho+bege, Penalty, Bolas, VRM/BGE10 novembro 2024 -
 Download Bakso Simulator (MOD, Unlimited Money) 1.7.4 APK for android10 novembro 2024
Download Bakso Simulator (MOD, Unlimited Money) 1.7.4 APK for android10 novembro 2024 -
 AONDE COMPRAR ROBUX BARATO !!10 novembro 2024
AONDE COMPRAR ROBUX BARATO !!10 novembro 2024 -
 Street Fighter: Akuma — Secret Compass10 novembro 2024
Street Fighter: Akuma — Secret Compass10 novembro 2024
