PDF] Power Consumption-based Detection of Sabotage Attacks in
Por um escritor misterioso
Last updated 23 dezembro 2024
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://d3i71xaburhd42.cloudfront.net/d81c8d2816032b4abc1798383f88d5a376d17a75/4-Figure1-1.png)
This work proposes a novel approach for detecting sabotage attacks in additive Manufacturing, based on continuous monitoring of the current delivered to all actuators during the manufacturing process and detection of deviations from a provable benign process. Additive Manufacturing (AM), a.k.a. 3D Printing, is increasingly used to manufacture functional parts of safety-critical systems. AM's dependence on computerization raises the concern that the AM process can be tampered with, and a part's mechanical properties sabotaged. This can lead to the destruction of a system employing the sabotaged part, causing loss of life, financial damage, and reputation loss. To address this threat, we propose a novel approach for detecting sabotage attacks. Our approach is based on continuous monitoring of the current delivered to all actuators during the manufacturing process and detection of deviations from a provable benign process. The proposed approach has numerous advantages: (i) it is non-invasive in a time-critical process, (ii) it can be retrofitted in legacy systems, and (iii) it is airgapped from the computerized components of the AM process, preventing simultaneous compromise. Evaluation on a desktop 3D Printer detects all attacks involving a modification of X or Y motor movement, with false positives at 0%.
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://pub.mdpi-res.com/computers/computers-12-00256/article_deploy/html/images/computers-12-00256-g004.png?1702023398)
Computers, Free Full-Text
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://d3i71xaburhd42.cloudfront.net/d81c8d2816032b4abc1798383f88d5a376d17a75/13-Figure9-1.png)
PDF] Power Consumption-based Detection of Sabotage Attacks in Additive Manufacturing
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://www.mdpi.com/jcp/jcp-02-00027/article_deploy/html/images/jcp-02-00027-g001.png)
JCP, Free Full-Text
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://www.researchgate.net/profile/Shih-Yuan-Yu/publication/339059143/figure/fig4/AS:855393400004611@1580953087286/Original-and-modified-wrench_Q320.jpg)
PDF) Sabotage Attack Detection for Additive Manufacturing Systems
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://media.springernature.com/lw685/springer-static/image/chp%3A10.1007%2F978-3-031-48652-4_15/MediaObjects/557569_1_En_15_Fig1_HTML.png)
Power Consumption Analysis as a Detection Indicator for Cyberattacks on Smart Home Devices
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://d3i71xaburhd42.cloudfront.net/d81c8d2816032b4abc1798383f88d5a376d17a75/8-Figure2-1.png)
PDF] Power Consumption-based Detection of Sabotage Attacks in Additive Manufacturing
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://www.gutenberg.org/files/26184/26184-h/images/cover.jpg)
The Project Gutenberg eBook of Simple Sabotage Field Manual, by Office of Strategic Services
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://www.frontiersin.org/files/Articles/591999/fenrg-08-591999-HTML-r1/image_m/fenrg-08-591999-g001.jpg)
Frontiers Using Design Thinking to Understand Cyber Attack Surfaces of Future Smart Grids
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://d3i71xaburhd42.cloudfront.net/507897340a3d52a6f4426e18dbe154e521a65802/77-Figure10-1.png)
PDF] Comparing Insider IT Sabotage and Espionage: A Model-Based Analysis
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://www.researchgate.net/profile/Shih-Yuan-Yu/publication/339059143/figure/fig2/AS:855393395806208@1580953086899/Attack-vectors-on-the-AM-process-chain_Q320.jpg)
PDF) Sabotage Attack Detection for Additive Manufacturing Systems
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://i1.rgstatic.net/publication/353266384_A_Novel_Insider_Attack_and_Machine_Learning_Based_Detection_for_the_Internet_of_Things/links/60fd34ad2bf3553b290de29c/largepreview.png)
PDF) A Novel Insider Attack and Machine Learning Based Detection for the Internet of Things
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://upload.wikimedia.org/wikipedia/commons/thumb/c/c8/SABOTAGE_CAN_OUTWEIGH_PRODUCTION_-_NARA_-_515321.jpg/1200px-SABOTAGE_CAN_OUTWEIGH_PRODUCTION_-_NARA_-_515321.jpg)
Sabotage - Wikipedia
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://image.slidesharecdn.com/lightsecforutilitiesandcriticalinfrastructurewhitepaper-160912065753/85/light-sec-for-utilities-and-critical-infrastructure-white-paper-1-320.jpg?cb=1670704168)
Light sec for utilities and critical infrastructure white paper
Recomendado para você
-
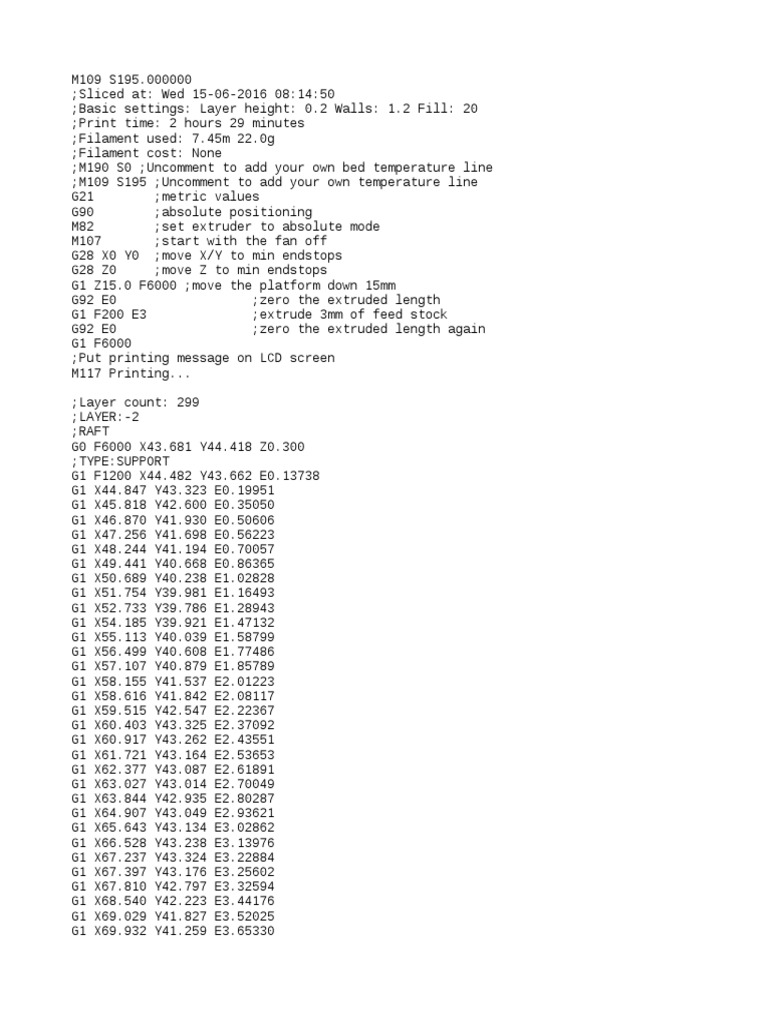
 3D Printing Forum - 3D Print Board23 dezembro 2024
3D Printing Forum - 3D Print Board23 dezembro 2024 -
 The illustration of G-code file format.23 dezembro 2024
The illustration of G-code file format.23 dezembro 2024 -
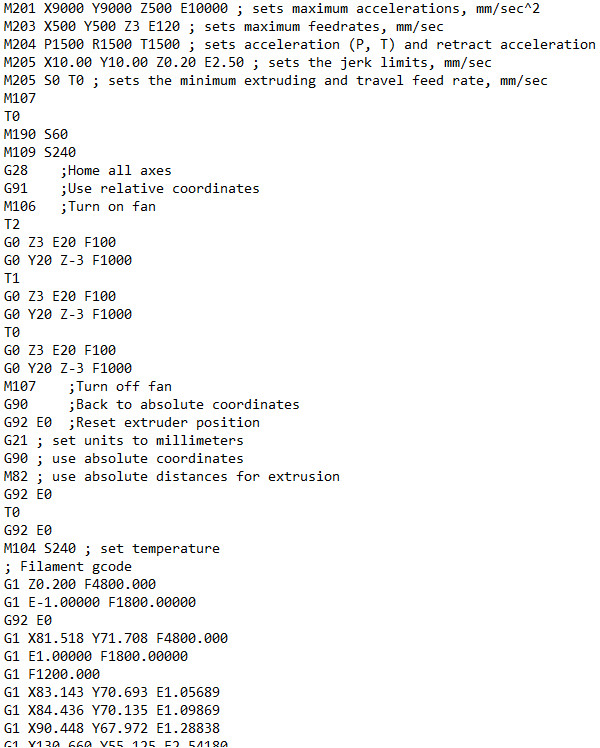
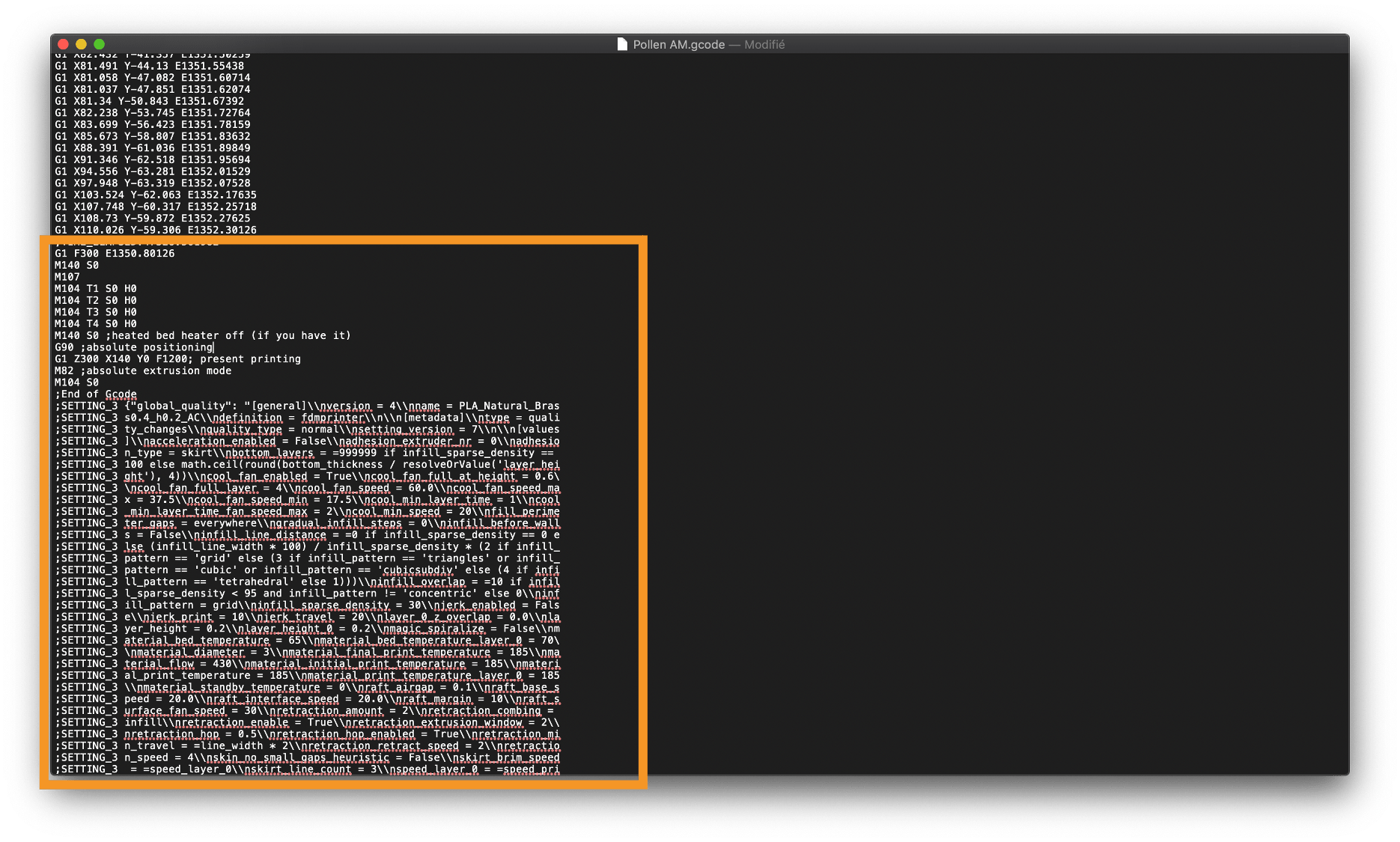 Pollen AM Edit G.code23 dezembro 2024
Pollen AM Edit G.code23 dezembro 2024 -
DeskProto - Feedrate for rotary machining: using G93 and G94 • The23 dezembro 2024
-
Cat, PDF23 dezembro 2024
-
 vba - Extract excel data to text file - Stack Overflow23 dezembro 2024
vba - Extract excel data to text file - Stack Overflow23 dezembro 2024 -
Simplify3D Software23 dezembro 2024
-
 Retraction distance error in prusaslicer/orcaslicer - Snapmaker J123 dezembro 2024
Retraction distance error in prusaslicer/orcaslicer - Snapmaker J123 dezembro 2024 -
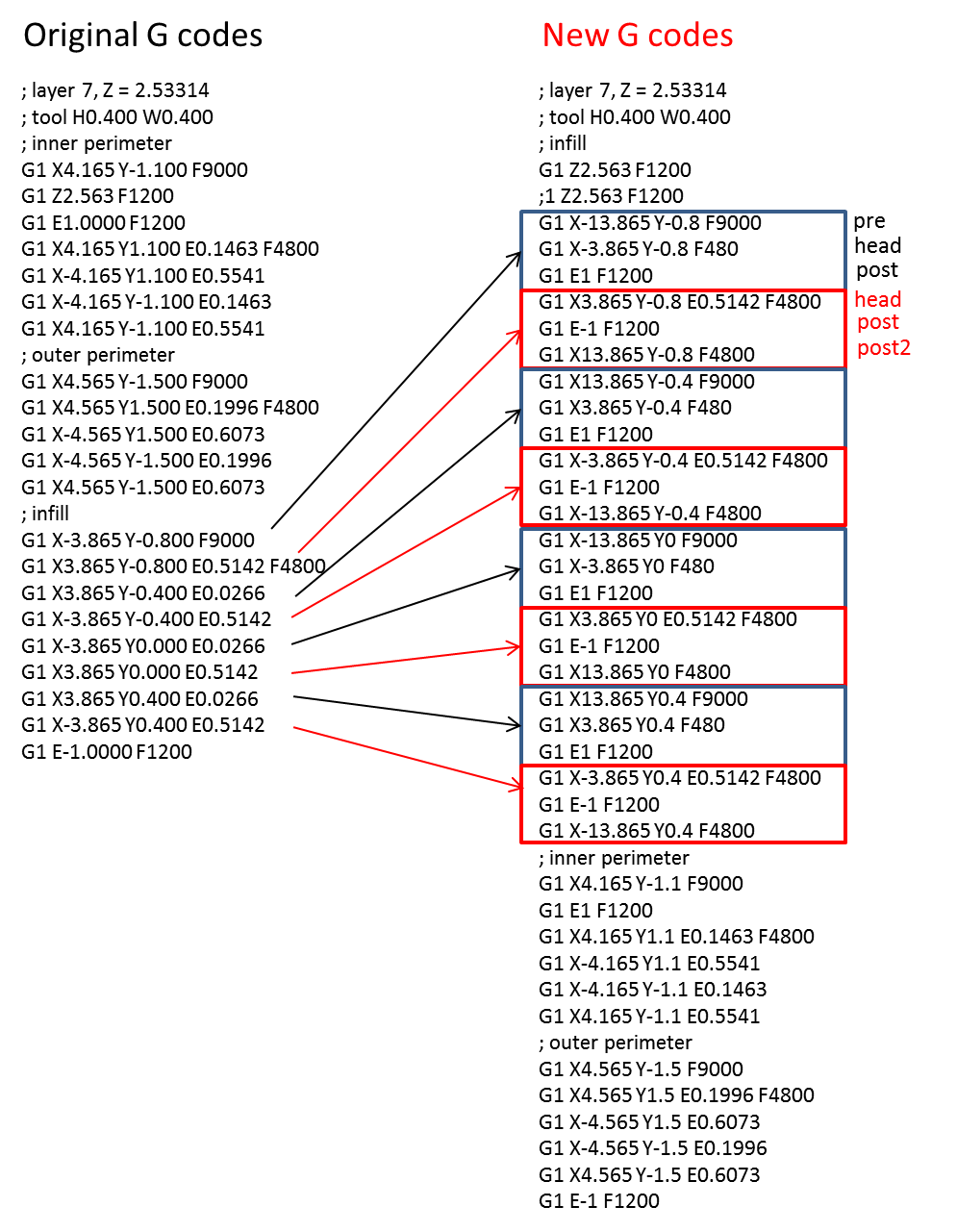 Tool Path Modification for 3D Printing: 3. Code – Learn As If You23 dezembro 2024
Tool Path Modification for 3D Printing: 3. Code – Learn As If You23 dezembro 2024 -
 G1 - BMW nacionaliza a R 1200 GS e preço baixa para R$ 69.900 - notícias em Motos23 dezembro 2024
G1 - BMW nacionaliza a R 1200 GS e preço baixa para R$ 69.900 - notícias em Motos23 dezembro 2024
você pode gostar
-
 Menos de 5€23 dezembro 2024
Menos de 5€23 dezembro 2024 -
 FÃ DO GERMAN CANO E DO JOHN KENNEDY🐻🇭🇺 on X: Pô ainda não to acreditando que não deram pênalti nisso aqui, o David Luiz claramente impede que a bola chegue no gol23 dezembro 2024
FÃ DO GERMAN CANO E DO JOHN KENNEDY🐻🇭🇺 on X: Pô ainda não to acreditando que não deram pênalti nisso aqui, o David Luiz claramente impede que a bola chegue no gol23 dezembro 2024 -
.jpeg) El ajedrez en los tiempos del covid23 dezembro 2024
El ajedrez en los tiempos del covid23 dezembro 2024 -
 fifa 23 player career mode build|TikTok Search23 dezembro 2024
fifa 23 player career mode build|TikTok Search23 dezembro 2024 -
Luana Mendes Rio de Janeiro RJ23 dezembro 2024
-
 BLOX FRUITS STRING AWAKENED + SUPERHUMAN 1 SHOT COMBO23 dezembro 2024
BLOX FRUITS STRING AWAKENED + SUPERHUMAN 1 SHOT COMBO23 dezembro 2024 -
 how to use blockposters.com download your poster - Canary Street Crafts23 dezembro 2024
how to use blockposters.com download your poster - Canary Street Crafts23 dezembro 2024 -
 Home - STREAM23 dezembro 2024
Home - STREAM23 dezembro 2024 -
 Twitch Prime goes global with exclusive gear in PLAYERUNKNOWN'S23 dezembro 2024
Twitch Prime goes global with exclusive gear in PLAYERUNKNOWN'S23 dezembro 2024 -
 How to Visit the Gerudo Secret Club Shop in Tears of the Kingdom23 dezembro 2024
How to Visit the Gerudo Secret Club Shop in Tears of the Kingdom23 dezembro 2024