Cybercriminals are circumventing email security with image-based
Por um escritor misterioso
Last updated 08 novembro 2024
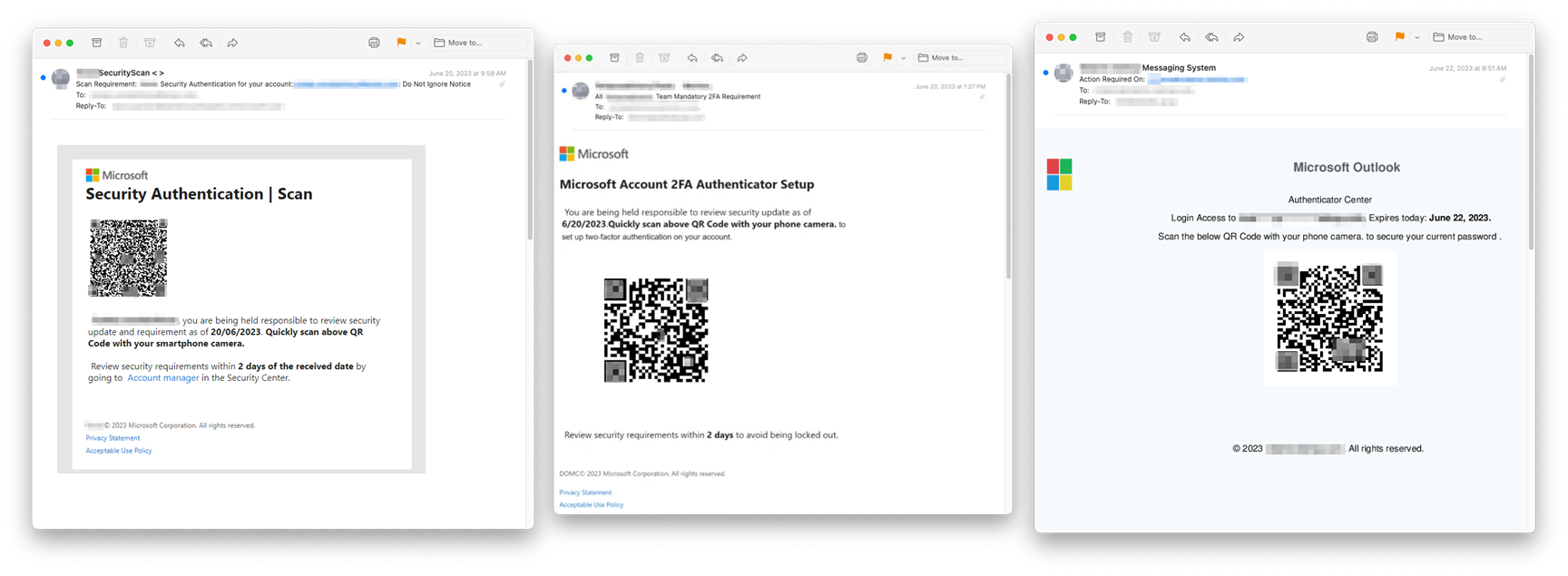
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't

Cybersecurity 101: Everything on how to protect your privacy and stay safe online
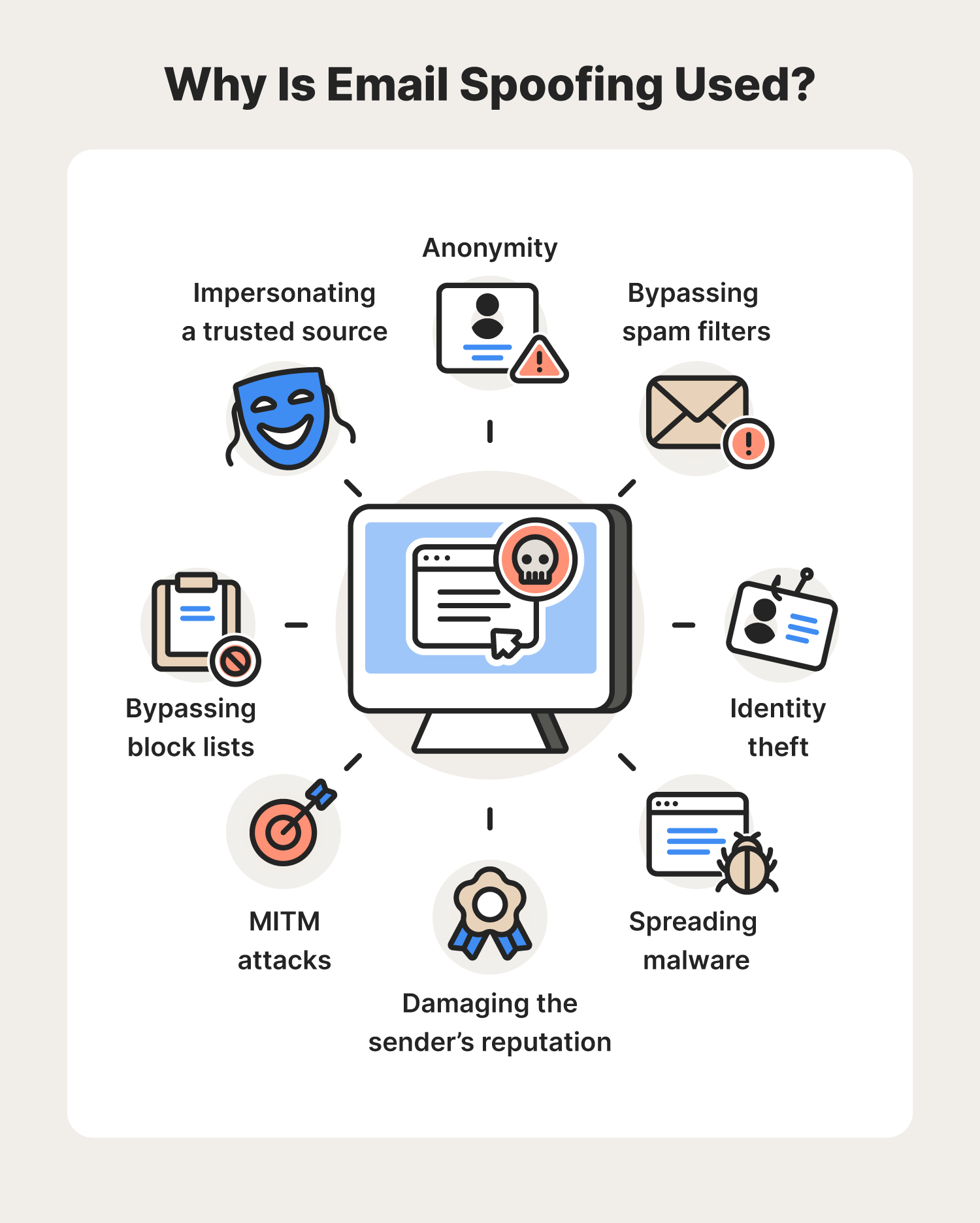
What is email spoofing? A complete guide - Norton

ITG23 Crypters Highlight Cooperation Between Cybercriminal Groups

A Shifting Email Conversation: Email Security is Stuck Looking to the Past
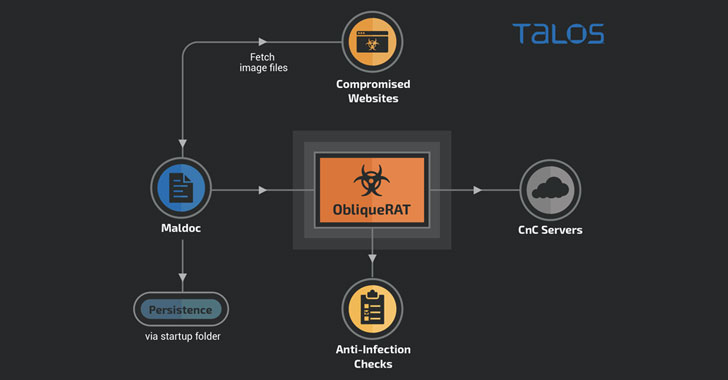
Hackers Now Hiding ObliqueRAT Payload in Images to Evade Detection

9 in 10 companies have experienced AI-enhanced email attacks, and continued use of AI will open up more risks—here's what you should know - Agility PR Solutions

Look But Don't Touch: Hackers Sending Targets Image-Based Phishing Scams

Cybercrime and AI : same threats now powered with advanced technology - Michalsons

Microsoft: BEC Attackers Evade 'Impossible Travel' Flags With Residential IP Addresses

Cybercriminals are circumventing email security with image-based scams

Four Ways Hackers are Outsmarting Retail Cybersecurity - Retail TouchPoints

What Is Email Security? Definition, Benefits, Examples & Best Practices - Spiceworks

Threat Actors Using Google AMP To Evade Phishing Attacks
Recomendado para você
-
 Murder Mystery 2 Codes (December 2023) - Knives, Gold & more08 novembro 2024
Murder Mystery 2 Codes (December 2023) - Knives, Gold & more08 novembro 2024 -
 All Evade Codes(Roblox) - Tested December 2022 - Player Assist08 novembro 2024
All Evade Codes(Roblox) - Tested December 2022 - Player Assist08 novembro 2024 -
 CODES – Evade! - Rick News08 novembro 2024
CODES – Evade! - Rick News08 novembro 2024 -
 NEW* ALL WORKING CODES FOR EVADE IN MARCH 2023! ROBLOX EVADE CODES08 novembro 2024
NEW* ALL WORKING CODES FOR EVADE IN MARCH 2023! ROBLOX EVADE CODES08 novembro 2024 -
 Codes Roblox Evolution Evade (août 2021)08 novembro 2024
Codes Roblox Evolution Evade (août 2021)08 novembro 2024 -
 NEW* ALL WORKING CODES FOR Evade IN OCTOBER 2023! ROBLOX Evade08 novembro 2024
NEW* ALL WORKING CODES FOR Evade IN OCTOBER 2023! ROBLOX Evade08 novembro 2024 -
 Redtrite08 novembro 2024
Redtrite08 novembro 2024 -
 Stranger Danger - Self-Defense, Escape & Evade08 novembro 2024
Stranger Danger - Self-Defense, Escape & Evade08 novembro 2024 -
Instagram photo by Derrick Van Orden • Oct 1, 2023 at 5:51 AM08 novembro 2024
-
Data Encoder Crypter08 novembro 2024
você pode gostar
-
 Estampa Xadrez Colorido - AVRO STORE08 novembro 2024
Estampa Xadrez Colorido - AVRO STORE08 novembro 2024 -
 Do tamanho de um cão', ratos estão cada vez maiores e dominam Nova York - Programa do Rochinha08 novembro 2024
Do tamanho de um cão', ratos estão cada vez maiores e dominam Nova York - Programa do Rochinha08 novembro 2024 -
 Netflix Dazzles With Parkour-Inspired Anime 'Bubble', From Original 'Attack on Titan' Studio08 novembro 2024
Netflix Dazzles With Parkour-Inspired Anime 'Bubble', From Original 'Attack on Titan' Studio08 novembro 2024 -
/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2019/T/j/qmFAvfT5i1Gdb4bTKiBw/screen-shot-2019-07-11-at-4.06.51-pm.png) Twitter caiu? Como saber se a rede está fora do ar08 novembro 2024
Twitter caiu? Como saber se a rede está fora do ar08 novembro 2024 -
 ACF FIORENTINA U19 X GENOA U19, Taça Primavera, AO VIVOASSISTA AGORA08 novembro 2024
ACF FIORENTINA U19 X GENOA U19, Taça Primavera, AO VIVOASSISTA AGORA08 novembro 2024 -
 ideia de skin emo08 novembro 2024
ideia de skin emo08 novembro 2024 -
 Anime girls kitagawa marin sono bisque doll wa koi wo Playmat Game Mat Desk08 novembro 2024
Anime girls kitagawa marin sono bisque doll wa koi wo Playmat Game Mat Desk08 novembro 2024 -
 ONE BLOCK LUCKY BLOCK in Minecraft Marketplace08 novembro 2024
ONE BLOCK LUCKY BLOCK in Minecraft Marketplace08 novembro 2024 -
 Terçol: causas, sintomas e tratamento08 novembro 2024
Terçol: causas, sintomas e tratamento08 novembro 2024 -
 Video Game Remixes08 novembro 2024
Video Game Remixes08 novembro 2024

