Hackers Using New Obfuscation Mechanisms to Evade Detection
Por um escritor misterioso
Last updated 31 dezembro 2024
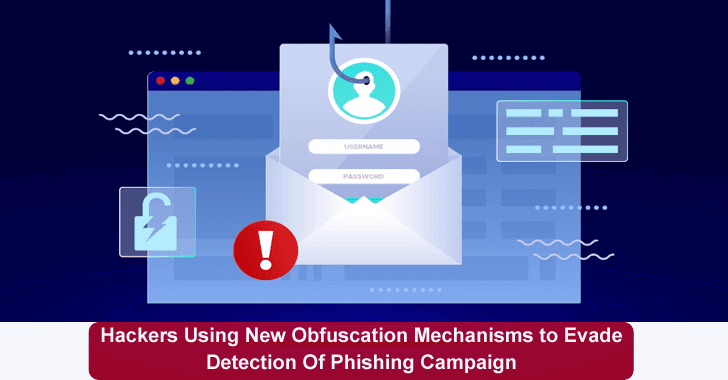
Recently, Microsoft has unveiled details of a deceptive social engineering campaign, in which the operators proceeded to change their obfuscation

BlueNoroff Hackers Utilize ObjCShellz Malware to Create Backdoors
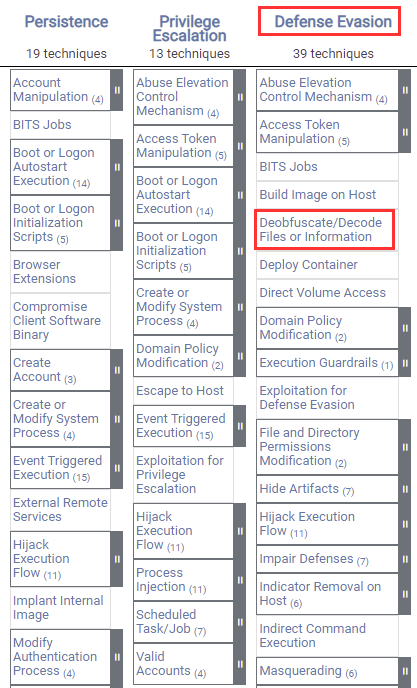
Windows Red Team Defense Evasion Techniques
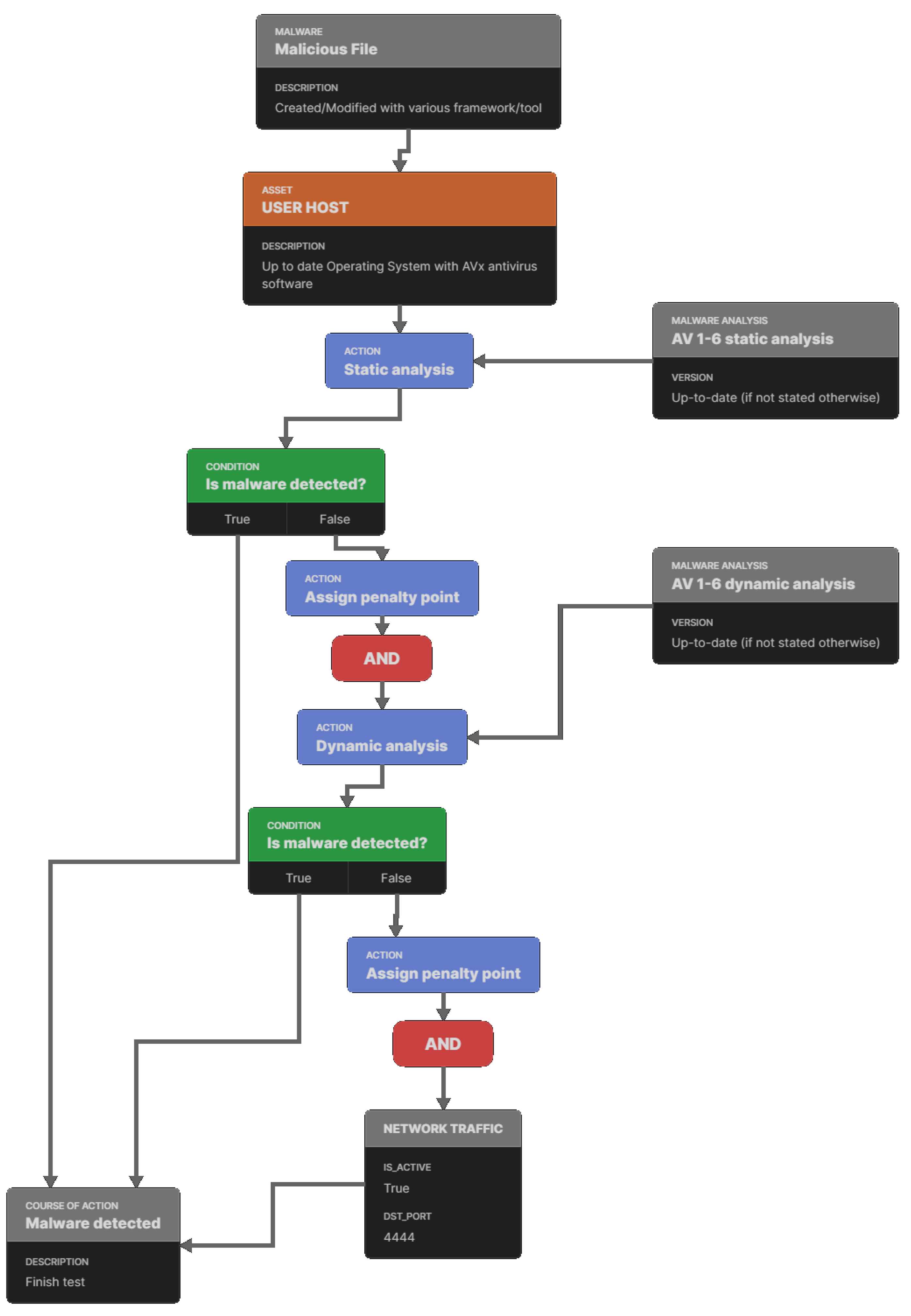
Applied Sciences, Free Full-Text

Web Application Obfuscation: '-/WAFs..Evasion..Filters//alert

Building coping mechanisms to deal with ransomware attacks across

UNC2565 threat actors continue to improve the GOOTLOADER malware

How Hackers Use Binary Padding to Outsmart Sandboxes

Diversification and obfuscation techniques for software security

Cybercriminals Using Powerful BatCloak Engine to Make Malware

BlackLotus UEFI Bootkit Detection: Exploits CVE-2022-21894 to

Lumma Stealer malware now uses trigonometry to evade detection

What is C2? Command and Control Infrastructure Explained

Healthcare System Notifies 180,000 People 1 Year After Hack
Recomendado para você
-
 Evade Roblox Hack: Money Farm, AFK Farm, ESP & More31 dezembro 2024
Evade Roblox Hack: Money Farm, AFK Farm, ESP & More31 dezembro 2024 -
 BlueNoroff How DPRK's macOS RustBucket Seeks to Evade Analysis31 dezembro 2024
BlueNoroff How DPRK's macOS RustBucket Seeks to Evade Analysis31 dezembro 2024 -
![OP Evade Script GUI [FREE]](https://vapouryt.co.uk/wp-content/uploads/2022/09/evade-script.jpg) OP Evade Script GUI [FREE]31 dezembro 2024
OP Evade Script GUI [FREE]31 dezembro 2024 -
 Evade Script Roblox – Auto Farm, Full Bright, ESP & More – Caked By Petite31 dezembro 2024
Evade Script Roblox – Auto Farm, Full Bright, ESP & More – Caked By Petite31 dezembro 2024 -
 evadescript31 dezembro 2024
evadescript31 dezembro 2024 -
 Compensation #2 for Parry / Evade Bug : r/ContestOfChampions31 dezembro 2024
Compensation #2 for Parry / Evade Bug : r/ContestOfChampions31 dezembro 2024 -
Evade GodMode, Speed, Fly, Gift Farm & more31 dezembro 2024
-
 Vidar Spyware Abuses CHM File Formats to Evade Detection31 dezembro 2024
Vidar Spyware Abuses CHM File Formats to Evade Detection31 dezembro 2024 -
New Cactus ransomware encrypts itself to evade antivirus31 dezembro 2024
-
 A Detailed Guide to QA Automation Testing31 dezembro 2024
A Detailed Guide to QA Automation Testing31 dezembro 2024
você pode gostar
-
 Cockpit Simulador Extreme Simracing31 dezembro 2024
Cockpit Simulador Extreme Simracing31 dezembro 2024 -
 Miles Edgeworth - Image Gallery, Ace Attorney Wiki31 dezembro 2024
Miles Edgeworth - Image Gallery, Ace Attorney Wiki31 dezembro 2024 -
 Final Stage: The Last Initial D Anime Series Airing in Japan31 dezembro 2024
Final Stage: The Last Initial D Anime Series Airing in Japan31 dezembro 2024 -
 1/6 Escala Masculino Soldado Mini Arma Arma Modelo Cena Acessórios Pistola Preta Brinquedo Para 12 Polegadas Figura De Ação Corpo - Figuras De Ação - AliExpress31 dezembro 2024
1/6 Escala Masculino Soldado Mini Arma Arma Modelo Cena Acessórios Pistola Preta Brinquedo Para 12 Polegadas Figura De Ação Corpo - Figuras De Ação - AliExpress31 dezembro 2024 -
 The Valorant Champions Meta of Istanbul - VCT 2022 - Champions Tour31 dezembro 2024
The Valorant Champions Meta of Istanbul - VCT 2022 - Champions Tour31 dezembro 2024 -
 The Joy Of Creation STORY FREE ROAM Is INSANE31 dezembro 2024
The Joy Of Creation STORY FREE ROAM Is INSANE31 dezembro 2024 -
Shagrath (Official) - Instagram : @ shagrathofficial31 dezembro 2024
-
 Ambush, Villains Wiki31 dezembro 2024
Ambush, Villains Wiki31 dezembro 2024 -
 PETS EDITOR🐰 SECRET PROMO CODE🎁 in avatar world31 dezembro 2024
PETS EDITOR🐰 SECRET PROMO CODE🎁 in avatar world31 dezembro 2024 -
 Menina e mulher engraçadas com fantasias de bruxas para o dia das bruxas31 dezembro 2024
Menina e mulher engraçadas com fantasias de bruxas para o dia das bruxas31 dezembro 2024


