Cryptographic Keys 101: What They Are & How They Secure Data - Hashed Out by The SSL Store™
Por um escritor misterioso
Last updated 10 novembro 2024

Cryptographic keys, in combination with an encryption algorithm, disguise data (encryption) so only a special key can access it (decryption).

Cryptographic Keys 101: What They Are & How They Secure Data

Hashed Out by The SSL Store™
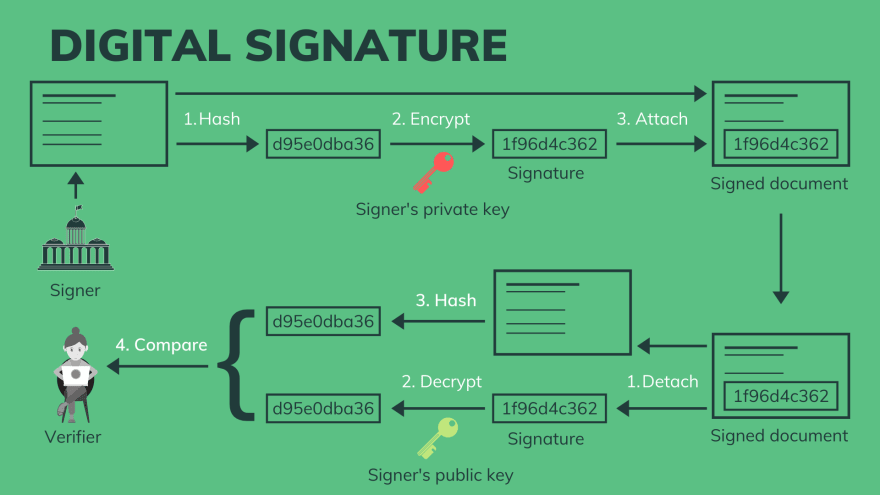
A complete overview of SSL/TLS and its cryptographic system - DEV

PII Encryption Protect Your Customer's Privacy
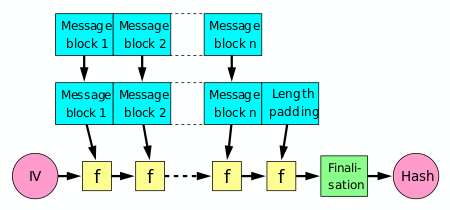
Cryptographic hash function - Wikipedia

Hashing vs. Encryption: Definitions & Differences - Okta SG

Cryptographic hash function - Wikipedia
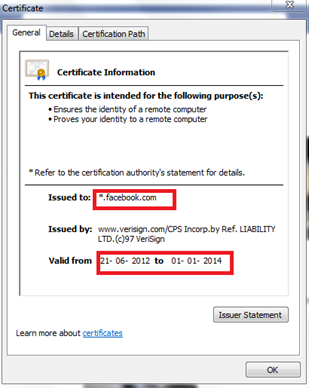
Cryptography 101 with SSL

What is a Pass-the-Hash Attack? - CrowdStrike
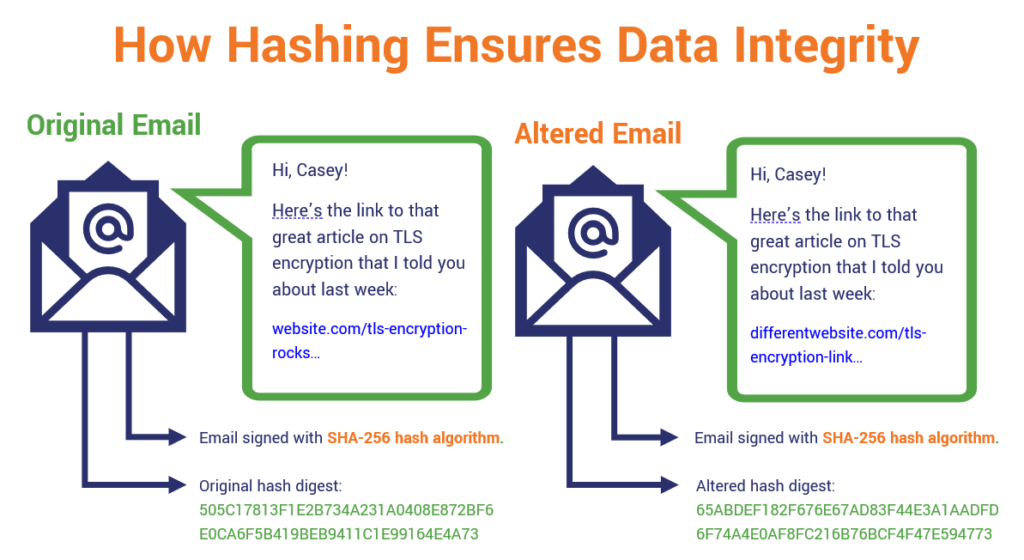
What Is a Hash Function in Cryptography? A Beginner's Guide
Recomendado para você
-
 Buy MX Keys S Keyboard - Full-Size10 novembro 2024
Buy MX Keys S Keyboard - Full-Size10 novembro 2024 -
 CompX Chicago 1250 - 1499 Keys10 novembro 2024
CompX Chicago 1250 - 1499 Keys10 novembro 2024 -
 Preferred Keys - BEST10 novembro 2024
Preferred Keys - BEST10 novembro 2024 -
 Lead in Keys Vermont Housing & Conservation Board10 novembro 2024
Lead in Keys Vermont Housing & Conservation Board10 novembro 2024 -
Titan Security Key - FIDO2 USB-A/USB-C + NFC10 novembro 2024
-
 Wicked Keys10 novembro 2024
Wicked Keys10 novembro 2024 -
 Types of keys - All Locks10 novembro 2024
Types of keys - All Locks10 novembro 2024 -
 The SpiKey attack: How to copy keys using sound10 novembro 2024
The SpiKey attack: How to copy keys using sound10 novembro 2024 -
 The Secret to Finding Lost Keys Revealed – Pebblebee10 novembro 2024
The Secret to Finding Lost Keys Revealed – Pebblebee10 novembro 2024 -
 Do Not Copy Keys - What it all means - Wynns Locksmiths10 novembro 2024
Do Not Copy Keys - What it all means - Wynns Locksmiths10 novembro 2024
você pode gostar
-
 18 Best Free Mac Games You Should Play in 202310 novembro 2024
18 Best Free Mac Games You Should Play in 202310 novembro 2024 -
 More Sonic CD sprites - Printable Version10 novembro 2024
More Sonic CD sprites - Printable Version10 novembro 2024 -
Boneca Arlequina Harley Quinn 30cm.10 novembro 2024
-
 Demonic Wisp in Blox Fruit - Blox Fruits10 novembro 2024
Demonic Wisp in Blox Fruit - Blox Fruits10 novembro 2024 -
 Ševčík gets first Czech call up, 11 Slavia players on international duty » SK Slavia Praha10 novembro 2024
Ševčík gets first Czech call up, 11 Slavia players on international duty » SK Slavia Praha10 novembro 2024 -
 Blue x green?? // Rainbow friends🌈💙//10 novembro 2024
Blue x green?? // Rainbow friends🌈💙//10 novembro 2024 -
 Jamshedpur to host Jharkhand State Open FIDE Rating Chess from10 novembro 2024
Jamshedpur to host Jharkhand State Open FIDE Rating Chess from10 novembro 2024 -
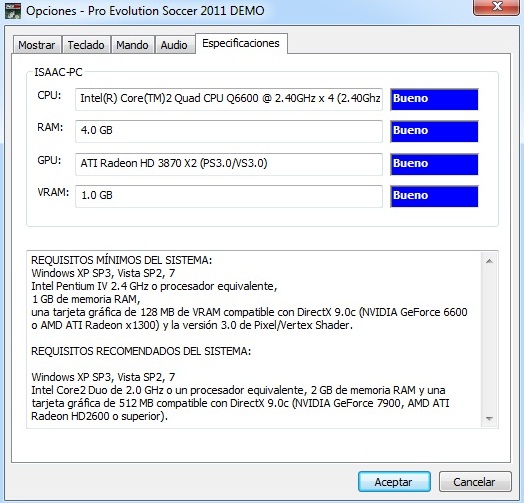 PES2011 PC: Requisitos10 novembro 2024
PES2011 PC: Requisitos10 novembro 2024 -
 Instant Gratification: “Pawn Sacrifice” and four other good movies10 novembro 2024
Instant Gratification: “Pawn Sacrifice” and four other good movies10 novembro 2024 -
![Deleted Scenes Fixes Pack [Counter-Strike: Condition Zero Deleted Scenes] [Mods]](https://images.gamebanana.com/img/ss/mods/5869e9c234dd2.webp) Deleted Scenes Fixes Pack [Counter-Strike: Condition Zero Deleted Scenes] [Mods]10 novembro 2024
Deleted Scenes Fixes Pack [Counter-Strike: Condition Zero Deleted Scenes] [Mods]10 novembro 2024
