Malware analysis Malicious activity
Por um escritor misterioso
Last updated 23 dezembro 2024
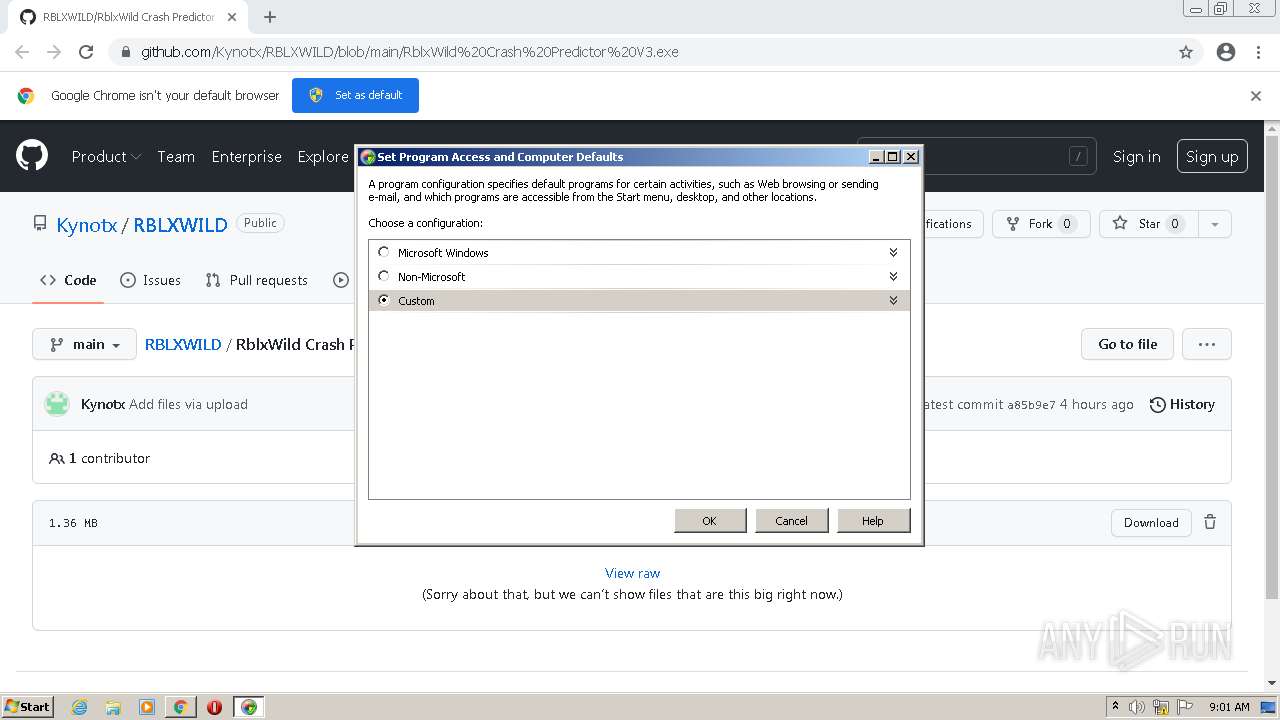

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog

Malware Analysis: Steps & Examples - CrowdStrike
Lab 6-1 Solutions - Practical Malware Analysis [Book]

What Is Malware Analysis? Definition, Types, Stages, and Best Practices - Spiceworks

Intro to Malware Analysis: What It Is & How It Works - InfoSec Insights

Malware Analysis: Steps & Examples - CrowdStrike

Malware Analysis: Protecting Your Network from Cyber Attacks
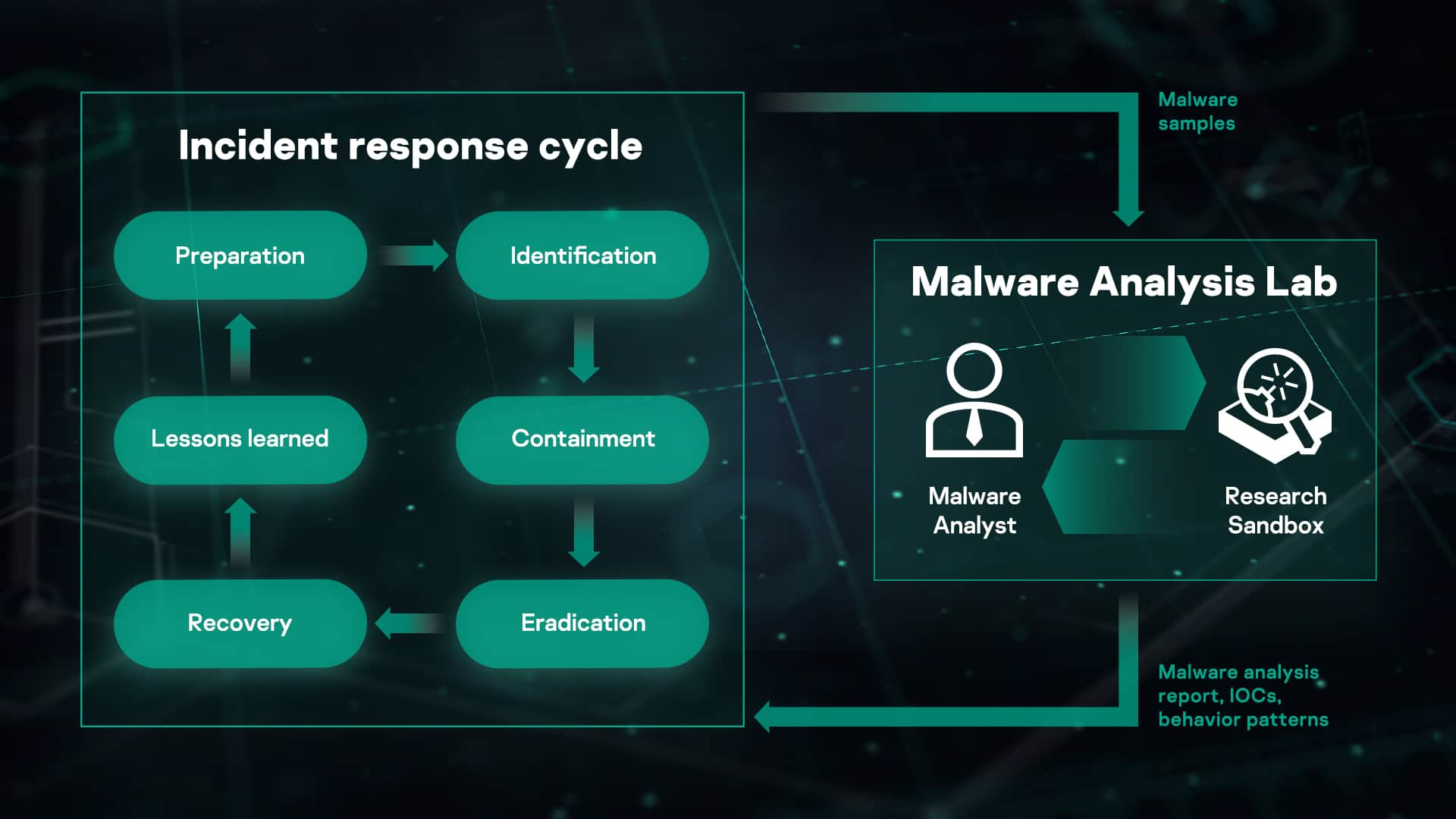
Advanced Automated Malware Analysis – Kaspersky Research Sandbox
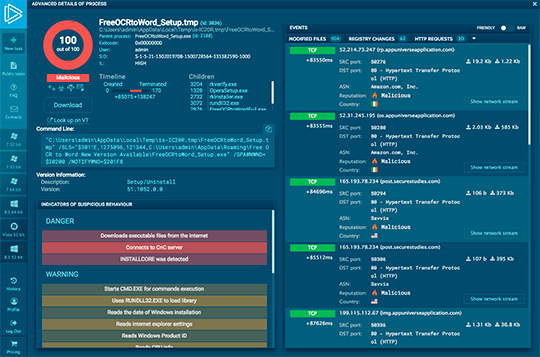
Interactive Online Malware Sandbox
Recomendado para você
-
 RBLXWild on X: And.. its another promo code 💰 Use code WildSj223 dezembro 2024
RBLXWild on X: And.. its another promo code 💰 Use code WildSj223 dezembro 2024 -
 rblxwild (FREE 100 ROBUX using code KASPT)23 dezembro 2024
rblxwild (FREE 100 ROBUX using code KASPT)23 dezembro 2024 -
 rblxwild promo codes 2023|Recherche TikTok23 dezembro 2024
rblxwild promo codes 2023|Recherche TikTok23 dezembro 2024 -
 0pen1n (@Va7ue1) / X23 dezembro 2024
0pen1n (@Va7ue1) / X23 dezembro 2024 -
kayra (@kayra09957640) / X23 dezembro 2024
-
100K rain on WILD! 🚀 #roblox #robloxfyp #robux #blοxflip #headless #k23 dezembro 2024
-
bloxflip · GitHub Topics · GitHub23 dezembro 2024
-
Rblxwild instant withdraw|TikTok Search23 dezembro 2024
-
 rblx wild predictor free discord|TikTok Search23 dezembro 2024
rblx wild predictor free discord|TikTok Search23 dezembro 2024 -
how to withdraw rbx on rblxwild|TikTok Search23 dezembro 2024
você pode gostar
-
 SuperEBA® EBA Cement23 dezembro 2024
SuperEBA® EBA Cement23 dezembro 2024 -
 Jogo de vídeo de dragão personagem pixelizada23 dezembro 2024
Jogo de vídeo de dragão personagem pixelizada23 dezembro 2024 -
 2024 HOT WHEELS Monster Trucks - Dodge Ram Van - Crash Legends - E75 – Toy Car Box23 dezembro 2024
2024 HOT WHEELS Monster Trucks - Dodge Ram Van - Crash Legends - E75 – Toy Car Box23 dezembro 2024 -
 Unown Weakness Pokemon Go - Best Raid & Leagues Counters23 dezembro 2024
Unown Weakness Pokemon Go - Best Raid & Leagues Counters23 dezembro 2024 -
 Idlewild Baptist Church23 dezembro 2024
Idlewild Baptist Church23 dezembro 2024 -
.jpg) Game-X Especial nº 18 – Retroavengers23 dezembro 2024
Game-X Especial nº 18 – Retroavengers23 dezembro 2024 -
 Connie Talbot from Britain's Got Talent: What she's up to now23 dezembro 2024
Connie Talbot from Britain's Got Talent: What she's up to now23 dezembro 2024 -
 Gym directory Map of Strength23 dezembro 2024
Gym directory Map of Strength23 dezembro 2024 -
 John Davison Rockefeller by Bettmann23 dezembro 2024
John Davison Rockefeller by Bettmann23 dezembro 2024 -
 Glitch Productions Acquire The Other Studios by melvin764g on DeviantArt23 dezembro 2024
Glitch Productions Acquire The Other Studios by melvin764g on DeviantArt23 dezembro 2024



