Malware analysis Malicious activity
Por um escritor misterioso
Last updated 08 novembro 2024

Malware Analysis: Protecting Your Network from Cyber Attacks

FBI, CISA, MS-ISAC release cybersecurity advisory on emerging
MetaDefender Cloud Advanced threat prevention and detection

Building A Simple Malware Analysis Pipeline In The Homelab Pt - 1

PROUD-MAL: static analysis-based progressive framework for deep

Security Orchestration Use Case: Automating Malware Analysis
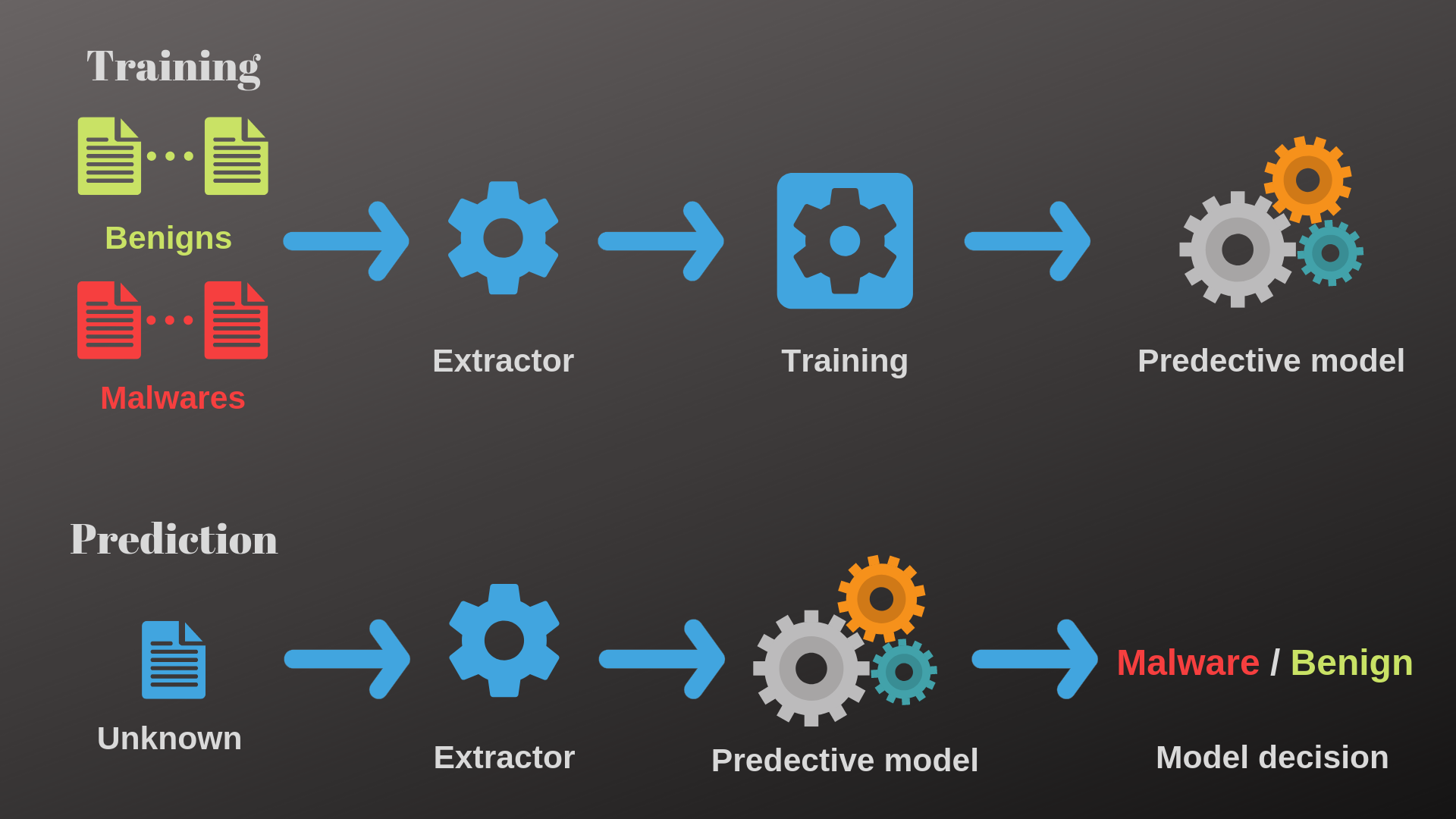
Feature Extraction and Detection of Malwares Using Machine
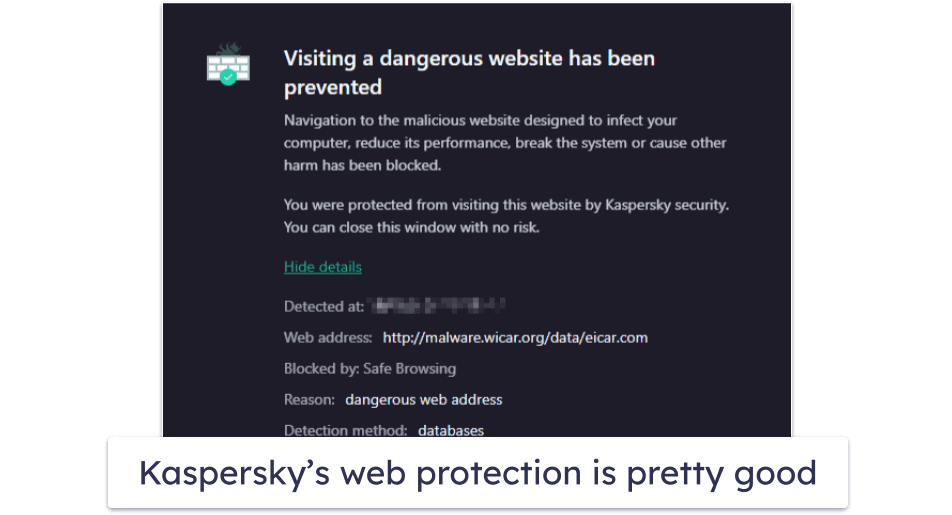
10 Best Antivirus Software in 2023: Windows, Android, iOS, Mac

10 Best Antivirus Software in 2023: Windows, Android, iOS, Mac

Detail procedure of malware analysis

Malware analysis file Malicious activity

Routers Roasting on an Open Firewall: the KV-botnet Investigation
Malware analysis AIO_4.9.8__ed.rar Malicious activity

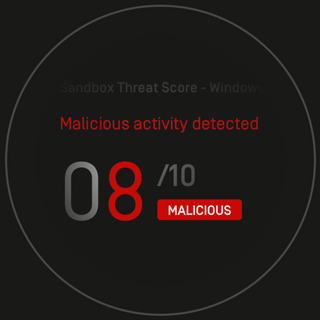
Interactive Online Malware Sandbox

How to Do Malware Analysis?
Recomendado para você
-
 Streamable Downloader & Streamable to mp4 converter08 novembro 2024
Streamable Downloader & Streamable to mp4 converter08 novembro 2024 -
 how to download a streamable video|TikTok Search08 novembro 2024
how to download a streamable video|TikTok Search08 novembro 2024 -
 Download Streamable Music album songs: Light08 novembro 2024
Download Streamable Music album songs: Light08 novembro 2024 -
 Patreon App Not Working w/ Streamable - Patreon Developers08 novembro 2024
Patreon App Not Working w/ Streamable - Patreon Developers08 novembro 2024 -
 The proposed streamable hybrid representation. A timedependent sliding08 novembro 2024
The proposed streamable hybrid representation. A timedependent sliding08 novembro 2024 -
 Streamable Online08 novembro 2024
Streamable Online08 novembro 2024 -
 Download Video from Streamable – Video Downloader Guru08 novembro 2024
Download Video from Streamable – Video Downloader Guru08 novembro 2024 -
 Streamable-67vwrj : tubeup.py : Free Download, Borrow, and Streaming : Internet Archive08 novembro 2024
Streamable-67vwrj : tubeup.py : Free Download, Borrow, and Streaming : Internet Archive08 novembro 2024 -
 How to Download TikTok Videos Without Watermark08 novembro 2024
How to Download TikTok Videos Without Watermark08 novembro 2024 -
How should I download Streamable videos? - Quora08 novembro 2024
você pode gostar
-
 Best chess24 Player in the World! Mug.08 novembro 2024
Best chess24 Player in the World! Mug.08 novembro 2024 -
 Hitori no Shita: The Outcast - Trailer Gameplay (Android/IOS08 novembro 2024
Hitori no Shita: The Outcast - Trailer Gameplay (Android/IOS08 novembro 2024 -
 Santo Anastacio, SP / BR, Clube dos Bancarios08 novembro 2024
Santo Anastacio, SP / BR, Clube dos Bancarios08 novembro 2024 -
 Boruto (manga) - Wikidata08 novembro 2024
Boruto (manga) - Wikidata08 novembro 2024 -
Sono Bisque Doll Wa Koi Wo Suru (Dublado) - - - - - - - - - - - - -08 novembro 2024
-
 Luffy Gear 2nd Luffy gear 2, Luffy, One piece crew08 novembro 2024
Luffy Gear 2nd Luffy gear 2, Luffy, One piece crew08 novembro 2024 -
 Love Emo Girls Heart Trendy Egirl Teens Goth Punk T-Shirt : Clothing, Shoes & Jewelry08 novembro 2024
Love Emo Girls Heart Trendy Egirl Teens Goth Punk T-Shirt : Clothing, Shoes & Jewelry08 novembro 2024 -
Do It Yourself - streaming tv show online08 novembro 2024
-
 Como fazer o levantamento terra convencional e terra sumô08 novembro 2024
Como fazer o levantamento terra convencional e terra sumô08 novembro 2024 -
 Kunsthåndværk08 novembro 2024
Kunsthåndværk08 novembro 2024

