Lab: Blind SSRF with Shellshock exploitation
Por um escritor misterioso
Last updated 23 dezembro 2024

This site uses analytics software which fetches the URL specified in the Referer header when a product page is loaded. To solve the lab, use this

翻译]盲SSRF利用链术语表-腾讯云开发者社区-腾讯云
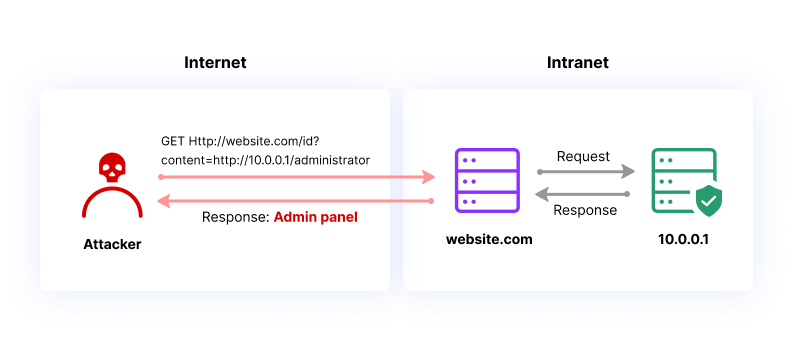
Server-Side Request Forgery (SSRF), Common Attacks & Risks

Gaining Access through Server-side Request Forgery

SSRF(服务器跨站请求伪造)基础知识- lca
Solving PortSwigger SSRF Labs - Final Part - ::: re:search + re
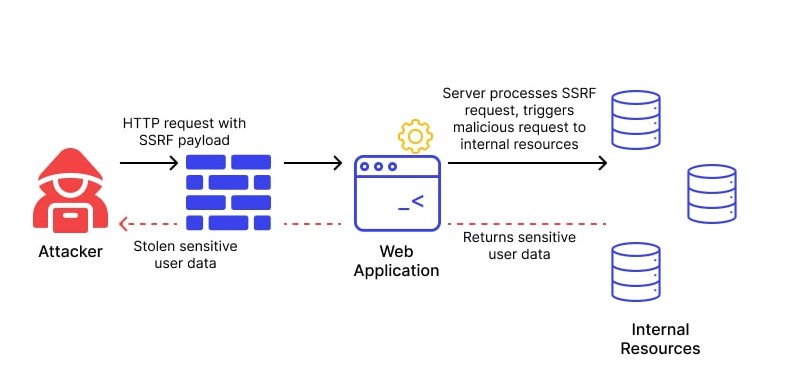
Website Hacking Archives - Hackercool Magazine

Blind SSRF exploitation ❗️ - Wallarm
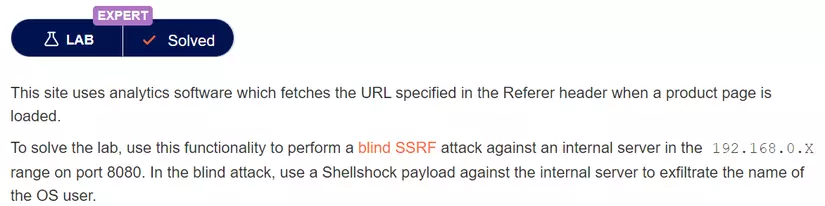
Server side request forgery vulnerabilities (SSRF) - Các lỗ hổng

Blind SSRF with Shellshock exploitationをやってみた - Shikata Ga Nai
Solving PortSwigger SSRF Labs - Final Part - ::: re:search + re
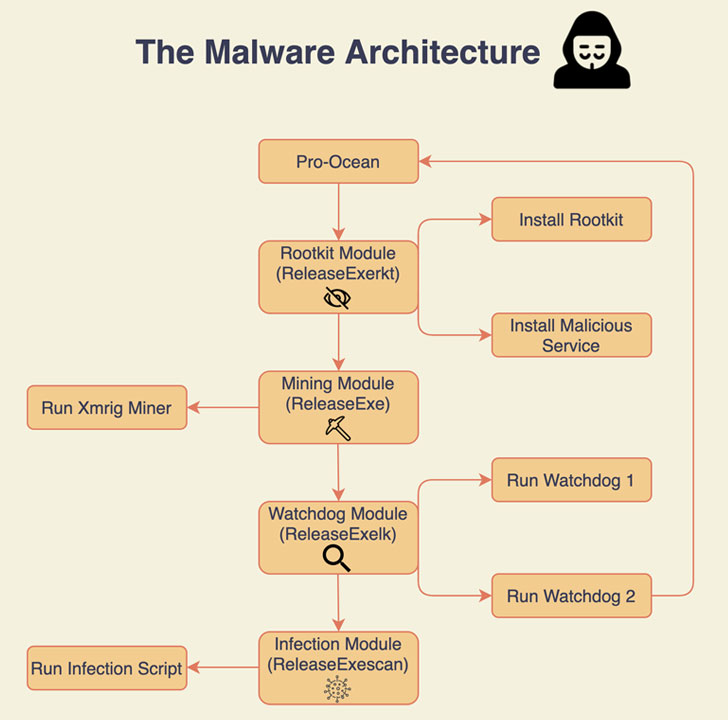
New Cryptojacking Malware Targeting Apache, Oracle, Redis Se

A GUIDE TO SERVER SIDE REQUEST FORGERY(SSRF) » Securityboat
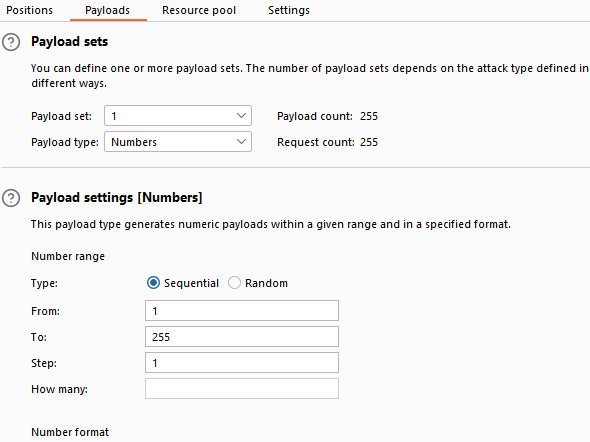
Portswigger Web Security Academy Lab: Blind SSRF with Shellshock
服务端请求伪造SSRF漏洞-7个实验(全)-云社区-华为云
Recomendado para você
-
 A new BASHLITE variant infects devices running BusyBox23 dezembro 2024
A new BASHLITE variant infects devices running BusyBox23 dezembro 2024 -
Romanian Hackers Used the Shellshock Bug to Hack Yahoo's Servers23 dezembro 2024
-
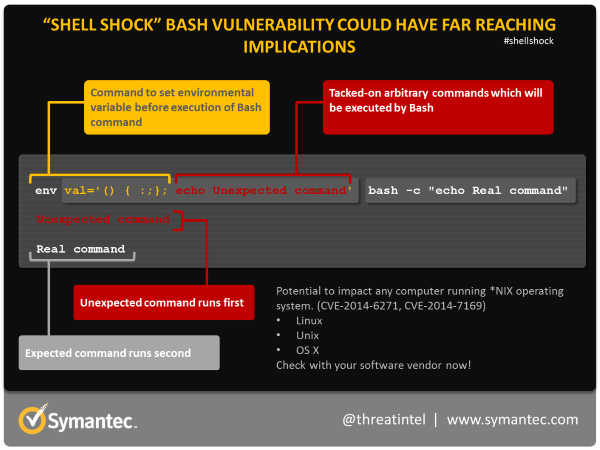 Threat Intelligence on X: Shellshock: All you need to know about the Bash Bug vulnerability #Shellshock #BashBug / X23 dezembro 2024
Threat Intelligence on X: Shellshock: All you need to know about the Bash Bug vulnerability #Shellshock #BashBug / X23 dezembro 2024 -
 Shellshock In-Depth: Why This Old Vulnerability Won't Go Away23 dezembro 2024
Shellshock In-Depth: Why This Old Vulnerability Won't Go Away23 dezembro 2024 -
Hackers already exploiting Shellshock flaw23 dezembro 2024
-
 Shellshock: Romanian hackers are accessing Yahoo servers, claims security expert, The Independent23 dezembro 2024
Shellshock: Romanian hackers are accessing Yahoo servers, claims security expert, The Independent23 dezembro 2024 -
 Shellshocked: Are You Prepared?23 dezembro 2024
Shellshocked: Are You Prepared?23 dezembro 2024 -
 BASHLITE Malware Uses ShellShock to Hijack Devices Running BusyBox - SecurityWeek23 dezembro 2024
BASHLITE Malware Uses ShellShock to Hijack Devices Running BusyBox - SecurityWeek23 dezembro 2024 -
Stephane Chazelas: the man who found the web's 'most dangerous' internet security bug23 dezembro 2024
-
 Are you suffering from ShellShock? - Infosec Partners23 dezembro 2024
Are you suffering from ShellShock? - Infosec Partners23 dezembro 2024
você pode gostar
-
 Counter-Strike : Condition Zero - Deleted Scenes Cover ( Final23 dezembro 2024
Counter-Strike : Condition Zero - Deleted Scenes Cover ( Final23 dezembro 2024 -
 Magnus Carlsen Chess Training on Play Magnus App: How to Play the Opening23 dezembro 2024
Magnus Carlsen Chess Training on Play Magnus App: How to Play the Opening23 dezembro 2024 -
 Will you press the button? APK for Android Download23 dezembro 2024
Will you press the button? APK for Android Download23 dezembro 2024 -
lieznerf's Profile23 dezembro 2024
-
 Laia on X: ✨ladies✨ / X23 dezembro 2024
Laia on X: ✨ladies✨ / X23 dezembro 2024 -
 Piccolo vs Pan Dragon Ball Super: SUPER HERO23 dezembro 2024
Piccolo vs Pan Dragon Ball Super: SUPER HERO23 dezembro 2024 -
 Jigsaw Junkies - Review: “Guardian Angel” by Educa, 7/1023 dezembro 2024
Jigsaw Junkies - Review: “Guardian Angel” by Educa, 7/1023 dezembro 2024 -
 Buy Tenjo Tenge online23 dezembro 2024
Buy Tenjo Tenge online23 dezembro 2024 -
 Comida realista - brinquedos comida jogo realista cozinha crianças23 dezembro 2024
Comida realista - brinquedos comida jogo realista cozinha crianças23 dezembro 2024 -
 ShopRite Named Most-Trusted Supermarket in the Northeast23 dezembro 2024
ShopRite Named Most-Trusted Supermarket in the Northeast23 dezembro 2024


