How Do MAC Spoofing Attacks Work?
Por um escritor misterioso
Last updated 08 janeiro 2025

In this blog, we will go into the complexities of MAC spoofing, analyzing its repercussions and emphasizing the importance of having strong security policies in place.

What is Spoofing? Spoofing Attacks Defined - CrowdStrike

ARP Spoofing: What Is the Aim of an ARP Spoofing Attack?
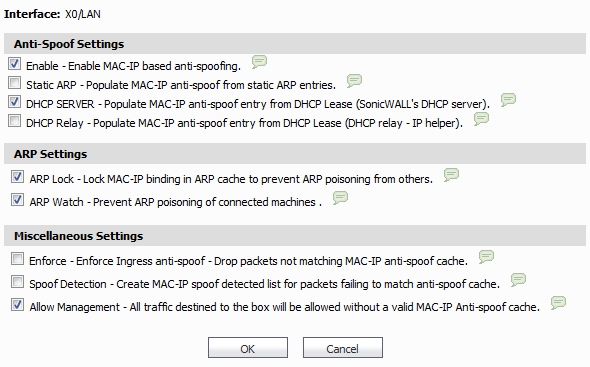
Configuring MAC-IP Anti-Spoof
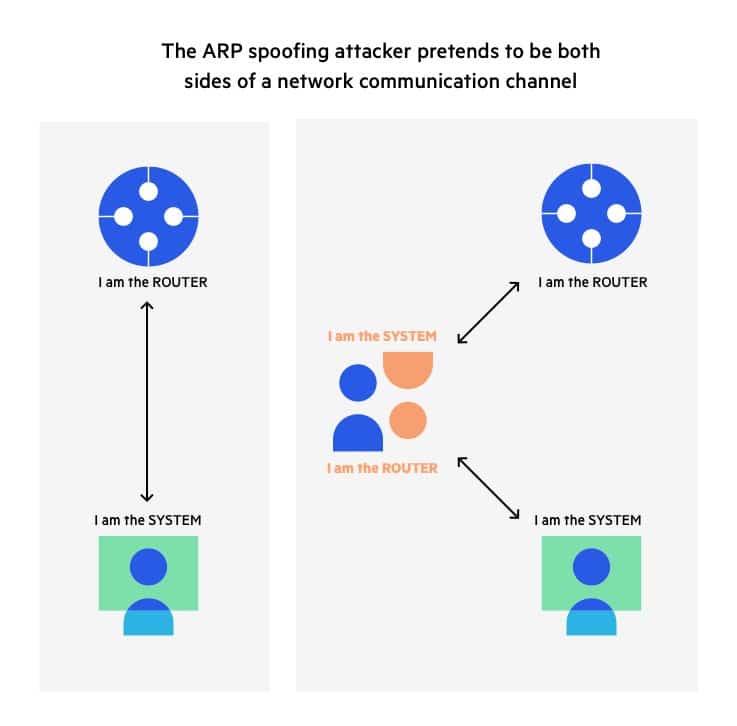
What is ARP Spoofing, ARP Cache Poisoning Attack Explained

What Is Address Resolution Protocol (ARP)?
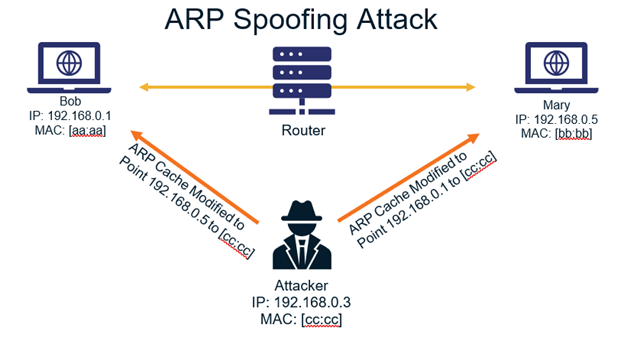
Everything You Need to Know About ARP Spoofing - Hashed Out by The SSL Store™

What Is a MAC Spoofing Attack and How Can You Prevent It?

ARP Spoofing - What is it and how can I protect myself?

What is Spoofing?, Examples & Prevention
Recomendado para você
-
 HOW TO REDEEM YOUR REDENGINE KEY AND DOWNLOAD REDENGINE!08 janeiro 2025
HOW TO REDEEM YOUR REDENGINE KEY AND DOWNLOAD REDENGINE!08 janeiro 2025 -
 meu cachorro morreu e agora não tenho dinheiro para spoofer no08 janeiro 2025
meu cachorro morreu e agora não tenho dinheiro para spoofer no08 janeiro 2025 -
 1PC In-line Fan Simulator Spoofer Remover for AntiMiner T9 T9 for08 janeiro 2025
1PC In-line Fan Simulator Spoofer Remover for AntiMiner T9 T9 for08 janeiro 2025 -
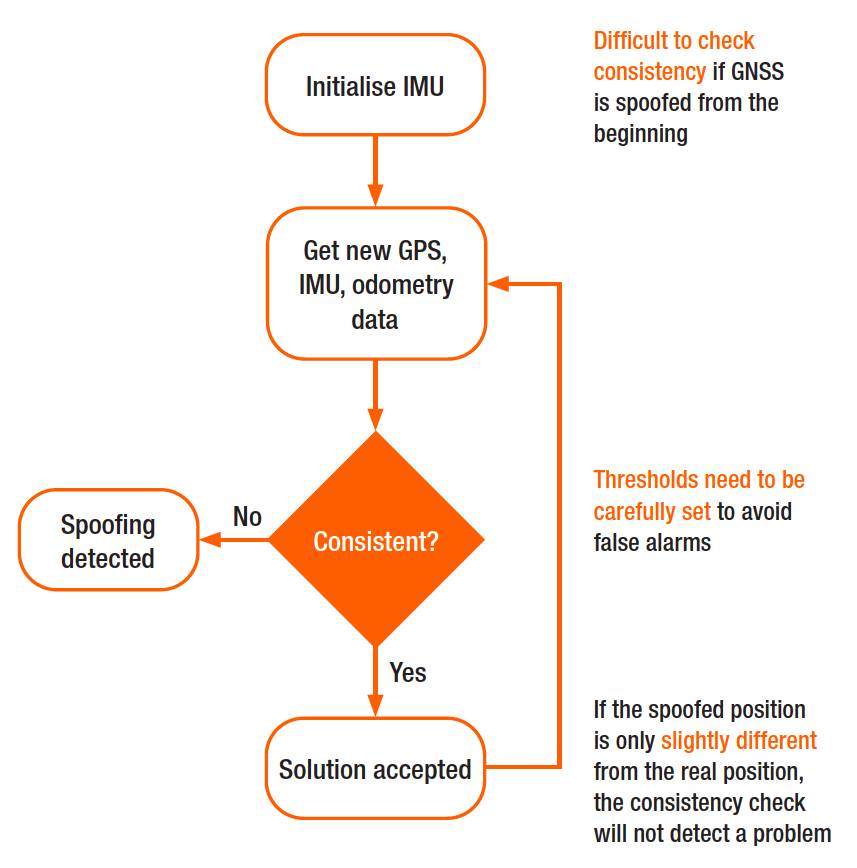 Why secure GPS receivers are crucial for GNSS/INS systems?08 janeiro 2025
Why secure GPS receivers are crucial for GNSS/INS systems?08 janeiro 2025 -
Hack The Seas Village - AIS Spoofing Attacks and Some Tools - TIB08 janeiro 2025
-
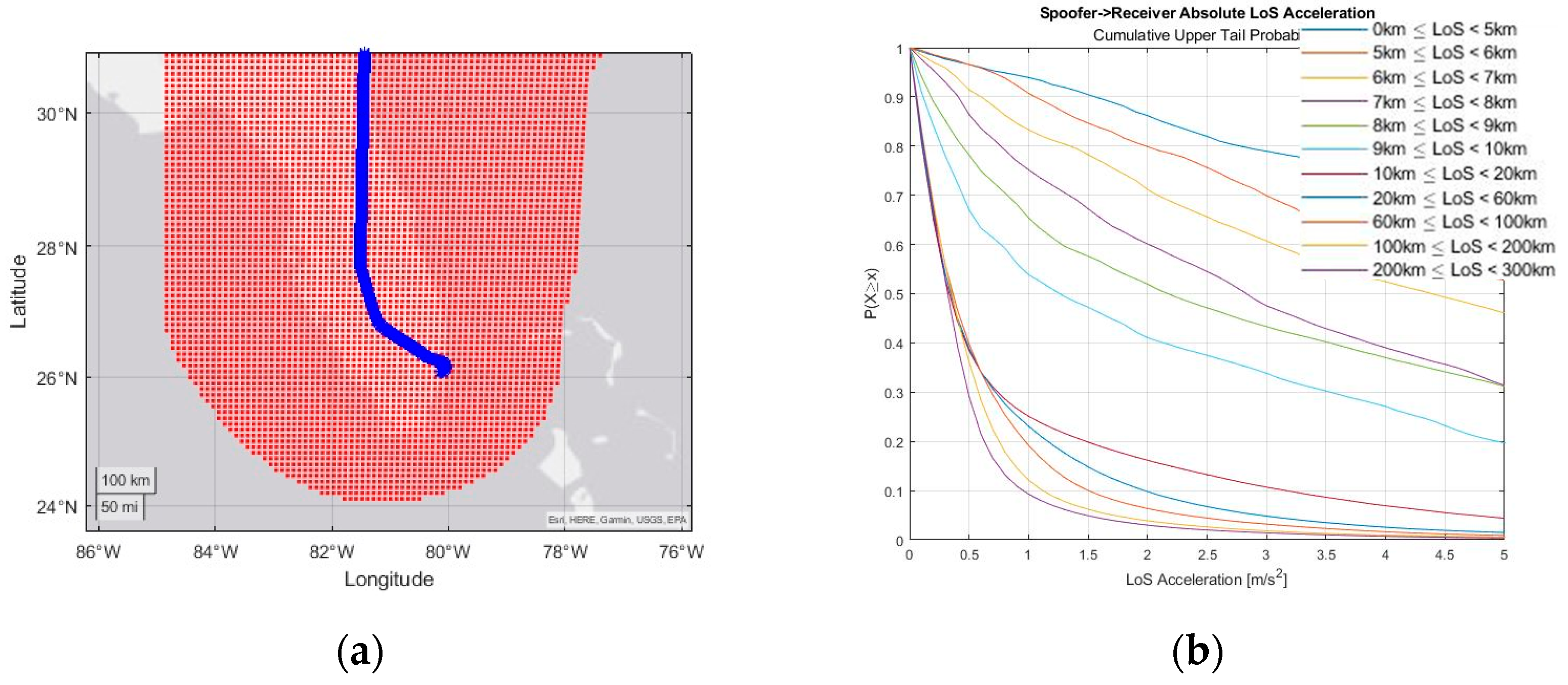 Engineering Proceedings, Free Full-Text08 janeiro 2025
Engineering Proceedings, Free Full-Text08 janeiro 2025 -
 Device Fingerprinting - SEON Docs08 janeiro 2025
Device Fingerprinting - SEON Docs08 janeiro 2025 -
![Release] rainbow - EFI bootkit like HWID spoofer (SMBIOS/disk/NIC)](https://i.imgur.com/hLGMoiB.png) Release] rainbow - EFI bootkit like HWID spoofer (SMBIOS/disk/NIC)08 janeiro 2025
Release] rainbow - EFI bootkit like HWID spoofer (SMBIOS/disk/NIC)08 janeiro 2025 -
 GitHub - sCANd3ww/RedEngineX: RedENGINE is the Best LUA Executor and Spoofer for FiveM with features Like: Premium Menu, Dumper, Stopper Ressource, Event Logger, Aimbot,ESP.08 janeiro 2025
GitHub - sCANd3ww/RedEngineX: RedENGINE is the Best LUA Executor and Spoofer for FiveM with features Like: Premium Menu, Dumper, Stopper Ressource, Event Logger, Aimbot,ESP.08 janeiro 2025 -
HookSpoofer: The Modified Open Source Stealer Bundlers Making the08 janeiro 2025
você pode gostar
-
 SEGA revela as últimas notícias de Sonic the Hedgehog08 janeiro 2025
SEGA revela as últimas notícias de Sonic the Hedgehog08 janeiro 2025 -
 Publicada a Nota Oficial 40/2023 – Alteração no local de competição da modalidade de vôlei de praia – JEMG/202308 janeiro 2025
Publicada a Nota Oficial 40/2023 – Alteração no local de competição da modalidade de vôlei de praia – JEMG/202308 janeiro 2025 -
 Why Did Online Gaming Star NetEase Advance More Than 25% in May? - TheStreet08 janeiro 2025
Why Did Online Gaming Star NetEase Advance More Than 25% in May? - TheStreet08 janeiro 2025 -
 Final Fantasy 7: Ever Crisis World Premiere Trailer08 janeiro 2025
Final Fantasy 7: Ever Crisis World Premiere Trailer08 janeiro 2025 -
 Do You Love Me (Now That I Can Dance) - Wikipedia08 janeiro 2025
Do You Love Me (Now That I Can Dance) - Wikipedia08 janeiro 2025 -
 Easter Egg Background png download - 496*600 - Free Transparent Egg png Download. - CleanPNG / KissPNG08 janeiro 2025
Easter Egg Background png download - 496*600 - Free Transparent Egg png Download. - CleanPNG / KissPNG08 janeiro 2025 -
 Fright Catalog – Insert Press08 janeiro 2025
Fright Catalog – Insert Press08 janeiro 2025 -
Featured Cosplay EP41: Ellie from The Last Of Us -- Superpixel08 janeiro 2025
-
 Jogos Mortais retorna aos cinemas com o décimo filme08 janeiro 2025
Jogos Mortais retorna aos cinemas com o décimo filme08 janeiro 2025 -
 Ink Sans png images08 janeiro 2025
Ink Sans png images08 janeiro 2025