HTB: Investigation
Por um escritor misterioso
Last updated 31 dezembro 2024

Investigation starts with a website that accepts user uploaded images and runs Exiftool on them. This version has a command injection. I’ll dig into that vulnerability, and then exploit it to get a foothold. Then I find a set of Windows event logs, and analyze them to extract a password. Finally, I find a piece of malware that runs as root and understand it to get execution.
Hack The Box: Keeper

After coming out, 'I had PTSD symptoms' says lay leader in church-plant
HTB-Investigation-CSDN博客

Part 3: How the HTB research was done and what's coming up in the main chapters. – Your name is like honey
HTB Walkthrough: Support - Cyber Gladius

Hack The Box Machine Write-Up: Keeper [Easy]

Investigation ( Hack the box). CVE-2022–23935, Microsoft Message…, by Fallen sky

Approach for investigating the photobinding of HTB to HSA.
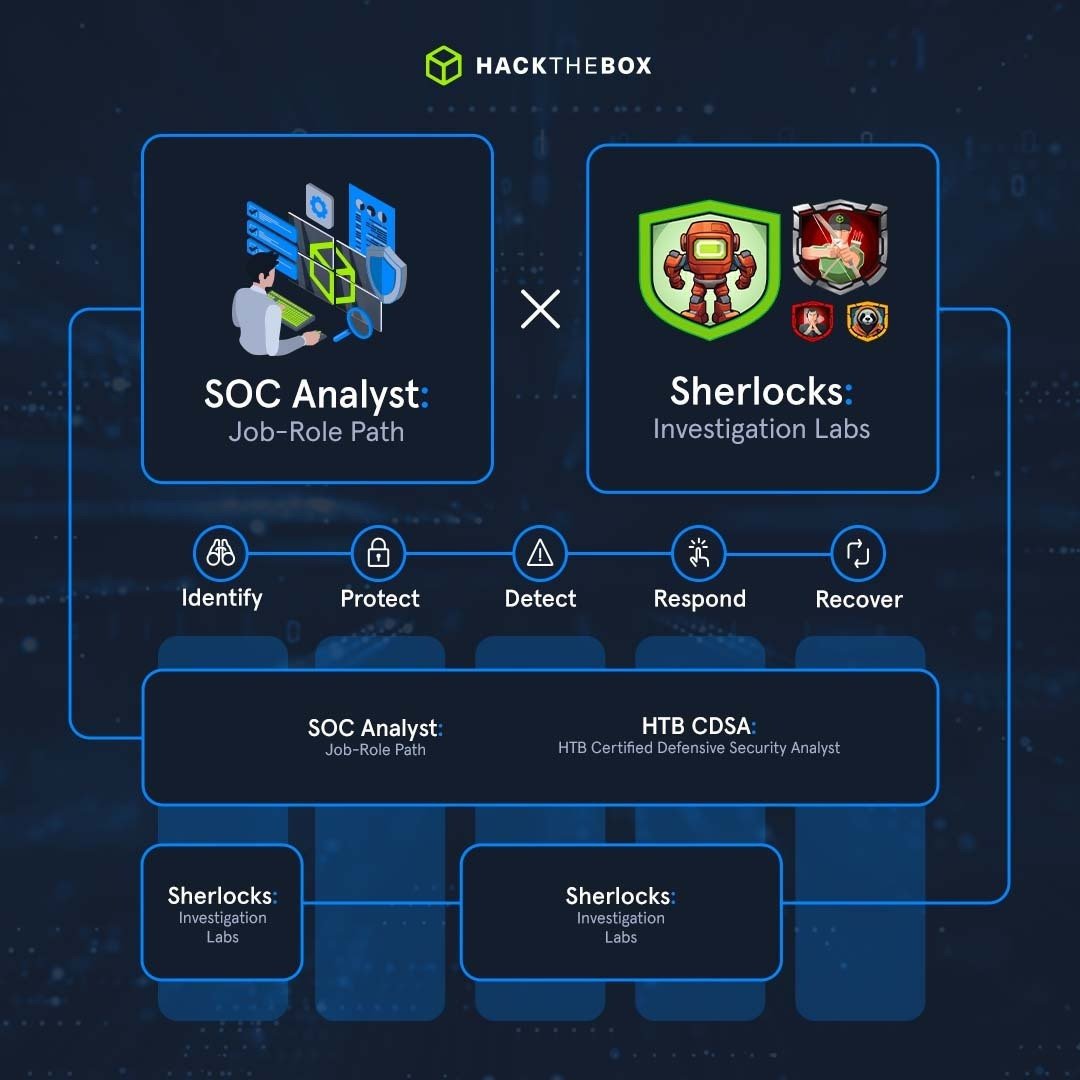
Enhance digital forensics and incident response (DFIR) skills with Sherlocks

How to buy police evidence management products (eBook)

HTB Investigation. The machine consist of exploiting…, by Damaidec
HTB: Investigation

Hack The Box
Recomendado para você
-
 Terraria on Steam31 dezembro 2024
Terraria on Steam31 dezembro 2024 -
 DigDig.io 🔥 Play online31 dezembro 2024
DigDig.io 🔥 Play online31 dezembro 2024 -
 Hacks - Dig Dug Arcade Edition31 dezembro 2024
Hacks - Dig Dug Arcade Edition31 dezembro 2024 -
![Dig Dug Redug [ROM HACK] by DragonDePlatino on DeviantArt](https://images-wixmp-ed30a86b8c4ca887773594c2.wixmp.com/f/9d5129b7-ce49-47de-9432-43876d118928/d7mhqba-68d06eb7-4dee-49a3-9ab8-651442703749.png?token=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJ1cm46YXBwOjdlMGQxODg5ODIyNjQzNzNhNWYwZDQxNWVhMGQyNmUwIiwiaXNzIjoidXJuOmFwcDo3ZTBkMTg4OTgyMjY0MzczYTVmMGQ0MTVlYTBkMjZlMCIsIm9iaiI6W1t7InBhdGgiOiJcL2ZcLzlkNTEyOWI3LWNlNDktNDdkZS05NDMyLTQzODc2ZDExODkyOFwvZDdtaHFiYS02OGQwNmViNy00ZGVlLTQ5YTMtOWFiOC02NTE0NDI3MDM3NDkucG5nIn1dXSwiYXVkIjpbInVybjpzZXJ2aWNlOmZpbGUuZG93bmxvYWQiXX0.L0JW1TM3YtaX4skBexTI84bmCJegianOmSZ7SO38QmU) Dig Dug Redug [ROM HACK] by DragonDePlatino on DeviantArt31 dezembro 2024
Dig Dug Redug [ROM HACK] by DragonDePlatino on DeviantArt31 dezembro 2024 -
 Cybersecurity method learns from hackers by tricking them31 dezembro 2024
Cybersecurity method learns from hackers by tricking them31 dezembro 2024 -
 Dig Bert (Dig Dug Hack - Q*Bert Mashup) - Atari 2600 Hacks31 dezembro 2024
Dig Bert (Dig Dug Hack - Q*Bert Mashup) - Atari 2600 Hacks31 dezembro 2024 -
Dig It Speed Jesus31 dezembro 2024
-
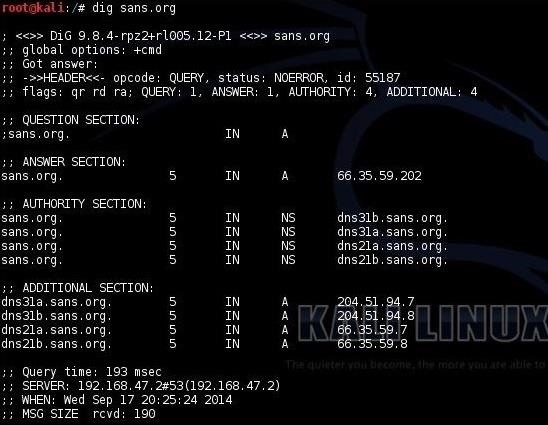 Hack Like a Pro: Abusing DNS for Reconnaissance « Null Byte :: WonderHowTo31 dezembro 2024
Hack Like a Pro: Abusing DNS for Reconnaissance « Null Byte :: WonderHowTo31 dezembro 2024 -
Onramp on X: Poor custody has resulted in ~$120B in crypto losses. A thread on what to watch out for & how to keep your assets safe / X31 dezembro 2024
-
 Urban traffic signal control robust optimization against Risk-averse and Worst-case cyberattacks - ScienceDirect31 dezembro 2024
Urban traffic signal control robust optimization against Risk-averse and Worst-case cyberattacks - ScienceDirect31 dezembro 2024
você pode gostar
-
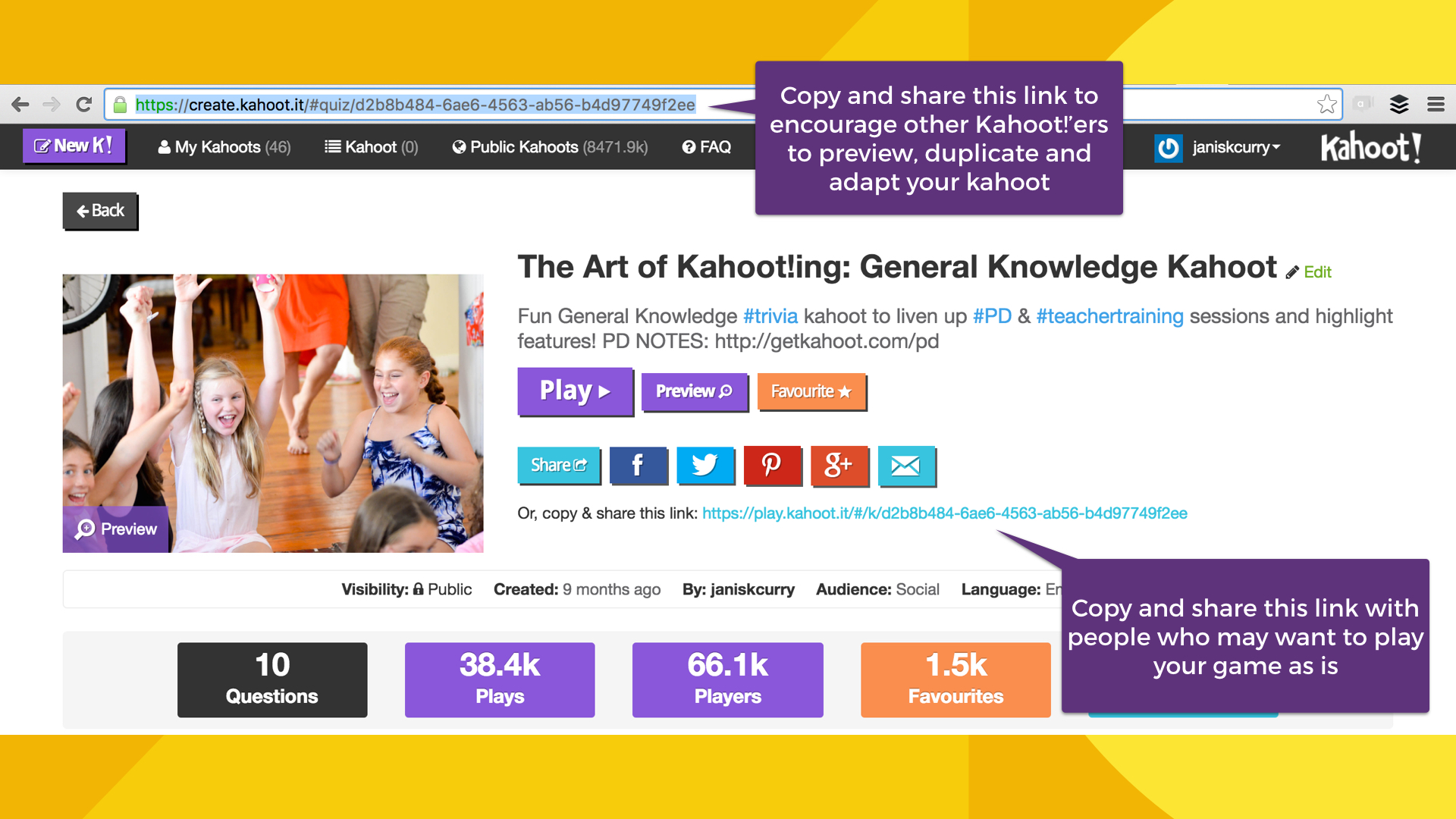 How to attract more Kahoot! players to your game31 dezembro 2024
How to attract more Kahoot! players to your game31 dezembro 2024 -
 Counter-Strike: Condition Zero achieves Linux compatibility31 dezembro 2024
Counter-Strike: Condition Zero achieves Linux compatibility31 dezembro 2024 -
 I Got HACKS in Roblox Bedwars?31 dezembro 2024
I Got HACKS in Roblox Bedwars?31 dezembro 2024 -
 The Sims 4 system requirements31 dezembro 2024
The Sims 4 system requirements31 dezembro 2024 -
 Isekai de Cheat Skill wo Te ni Shita Ore wa, Genjitsu Sekai wo mo Musou Suru: Level Up wa Jinsei wo Kaeta • I Got a Cheat Skill in Another World and31 dezembro 2024
Isekai de Cheat Skill wo Te ni Shita Ore wa, Genjitsu Sekai wo mo Musou Suru: Level Up wa Jinsei wo Kaeta • I Got a Cheat Skill in Another World and31 dezembro 2024 -
 Jio cloud gaming tech enables to play high-end games on entry-level 5G phones - The Samikhsya31 dezembro 2024
Jio cloud gaming tech enables to play high-end games on entry-level 5G phones - The Samikhsya31 dezembro 2024 -
1°detonado Yellow, PDF, Pokémon31 dezembro 2024
-
 Who is the best guitar hero character and why is Midori? : r31 dezembro 2024
Who is the best guitar hero character and why is Midori? : r31 dezembro 2024 -
 Ocupação de estádios na Rússia está abaixo de 50% - 01/04/2018 - Esporte - Folha31 dezembro 2024
Ocupação de estádios na Rússia está abaixo de 50% - 01/04/2018 - Esporte - Folha31 dezembro 2024 -
 Kit 4 Capa Protetora Controle Playstation Ps5 Game Silicone Azul31 dezembro 2024
Kit 4 Capa Protetora Controle Playstation Ps5 Game Silicone Azul31 dezembro 2024