Detecting Linux Anti-Forensics: Timestomping
Por um escritor misterioso
Last updated 21 dezembro 2024
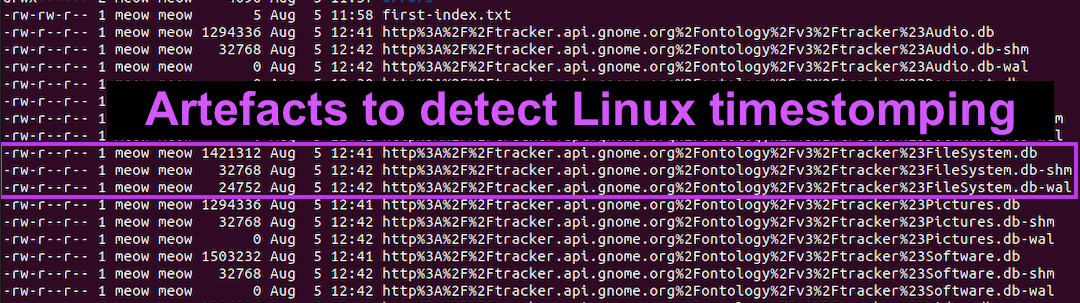
#160; Threat actors can modify the timestamps on malicious files to evade detection. This technique has been used time and time again across va
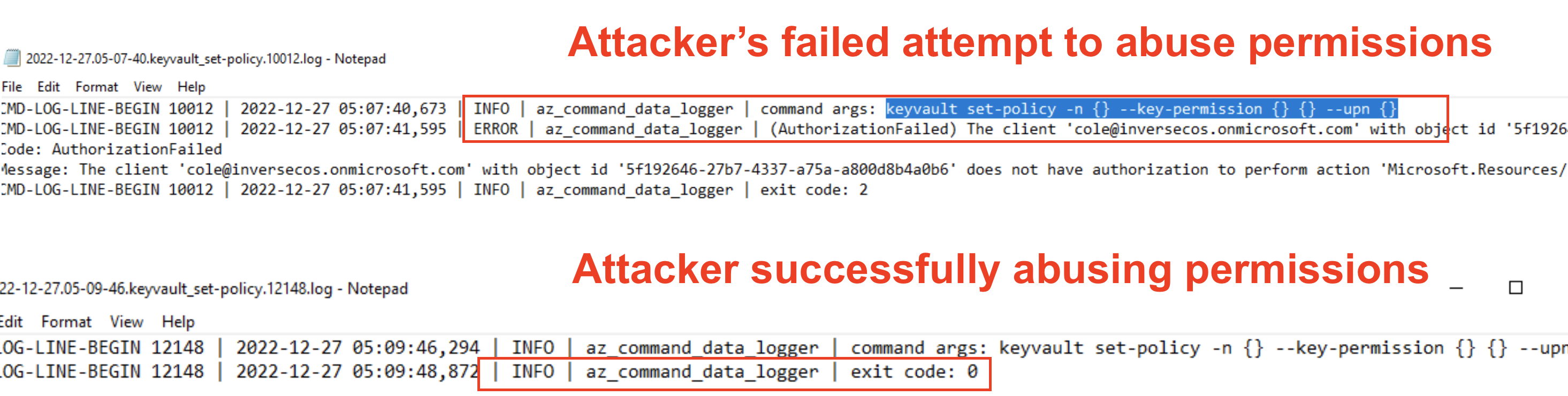
Detecting Linux Anti-Forensics: Timestomping

Wiping Techniques and Anti-Forensics Methods
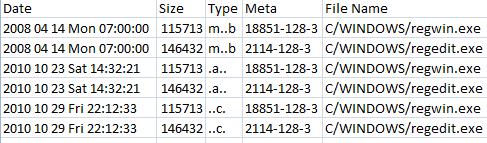
SANS Digital Forensics and Incident Response Blog
Anti-Forensic Techniques Used By Lazarus Group - ASEC BLOG

PDF) A survey on anti-forensics techniques

Anti-forensics Securing Network Infrastructure

Anti-forensics: Furthering digital forensic science through a new

Lina L. en LinkedIn: Detecting Linux Anti-Forensics: Timestomping

NTFS. - ppt download
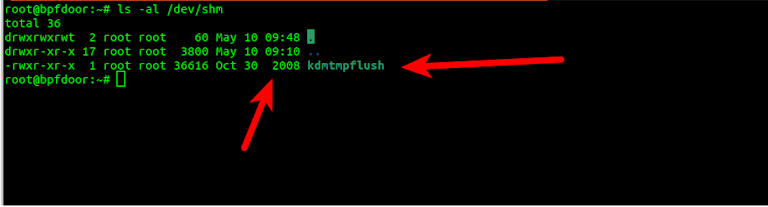
BPFDoor - An Evasive Linux Backdoor Technical Analysis

Anti-Forensic: Swipe Footprint with Timestomp - Hacking Articles

Lina L. en LinkedIn: Detecting Linux Anti-Forensics: Timestomping
Recomendado para você
-
Apollo Evade Mens Mountain Bike - S, M, L, XL Frames21 dezembro 2024
-
 KAT Script Download For Windows PC - Softlay21 dezembro 2024
KAT Script Download For Windows PC - Softlay21 dezembro 2024 -
I love evade.#fyp#viral#evade#mobilegameplay #iloveevade, a+w+d evade21 dezembro 2024
-
![OP Evade Script GUI [FREE]](https://vapouryt.co.uk/wp-content/uploads/2022/09/evade-script.jpg) OP Evade Script GUI [FREE]21 dezembro 2024
OP Evade Script GUI [FREE]21 dezembro 2024 -
 Reference attack model: an attacker embeds a malicious script into21 dezembro 2024
Reference attack model: an attacker embeds a malicious script into21 dezembro 2024 -
 PhantomScript #1 League Of Legends Script21 dezembro 2024
PhantomScript #1 League Of Legends Script21 dezembro 2024 -
 Tbao Hub Evade Mobile Script21 dezembro 2024
Tbao Hub Evade Mobile Script21 dezembro 2024 -
 RedLine Stealer : A new variant surfaces, Deploying using Batch Script - CYFIRMA21 dezembro 2024
RedLine Stealer : A new variant surfaces, Deploying using Batch Script - CYFIRMA21 dezembro 2024 -
 Netflix Clone - Video Streaming App - Launch OTT Platform - Develop The Most Sophisticated Netflix Clone With AiOC- Netflix Clone Script - SideProjectors21 dezembro 2024
Netflix Clone - Video Streaming App - Launch OTT Platform - Develop The Most Sophisticated Netflix Clone With AiOC- Netflix Clone Script - SideProjectors21 dezembro 2024 -
 Evade APK for Android Download21 dezembro 2024
Evade APK for Android Download21 dezembro 2024
você pode gostar
-
 Jogo Da Memória Bichos e Fillhotes Educativo Pedagógico com 54 Peças21 dezembro 2024
Jogo Da Memória Bichos e Fillhotes Educativo Pedagógico com 54 Peças21 dezembro 2024 -
 Pokemon série quebra-cabeça dos desenhos animados pikachu anime jogos e quebra-cabeças takara tomy brinquedos para crianças inquietas para crianças jogo de quebra-cabeça - AliExpress21 dezembro 2024
Pokemon série quebra-cabeça dos desenhos animados pikachu anime jogos e quebra-cabeças takara tomy brinquedos para crianças inquietas para crianças jogo de quebra-cabeça - AliExpress21 dezembro 2024 -
 Apollo Justice: Ace Attorney Trilogy - Preview - PSX Brasil21 dezembro 2024
Apollo Justice: Ace Attorney Trilogy - Preview - PSX Brasil21 dezembro 2024 -
 Top games tagged browser21 dezembro 2024
Top games tagged browser21 dezembro 2024 -
 Anime memes on X: Another anime rule. Link21 dezembro 2024
Anime memes on X: Another anime rule. Link21 dezembro 2024 -
 Pichu Evolutions Pokemon pikachu evolution, Pikachu wallpaper iphone, Pikachu evolution21 dezembro 2024
Pichu Evolutions Pokemon pikachu evolution, Pikachu wallpaper iphone, Pikachu evolution21 dezembro 2024 -
 One Piece: World Seeker DLC Episode 3 'The Unfinished Map' first screenshots - Gematsu21 dezembro 2024
One Piece: World Seeker DLC Episode 3 'The Unfinished Map' first screenshots - Gematsu21 dezembro 2024 -
 Hitoribocchi no Maru Maru Seikatsu 7 (Dengeki Comics NEXT)21 dezembro 2024
Hitoribocchi no Maru Maru Seikatsu 7 (Dengeki Comics NEXT)21 dezembro 2024 -
 Óculos De Sol Masculino Original Juliet Espelhado Barato Armação21 dezembro 2024
Óculos De Sol Masculino Original Juliet Espelhado Barato Armação21 dezembro 2024 -
 Amagami SS – Primeiras impressões21 dezembro 2024
Amagami SS – Primeiras impressões21 dezembro 2024

