Cryptojacking - Cryptomining in the browser — ENISA
Por um escritor misterioso
Last updated 22 dezembro 2024

The technique of hijacking browsers for mining cryptocurrency (without user consent) is called
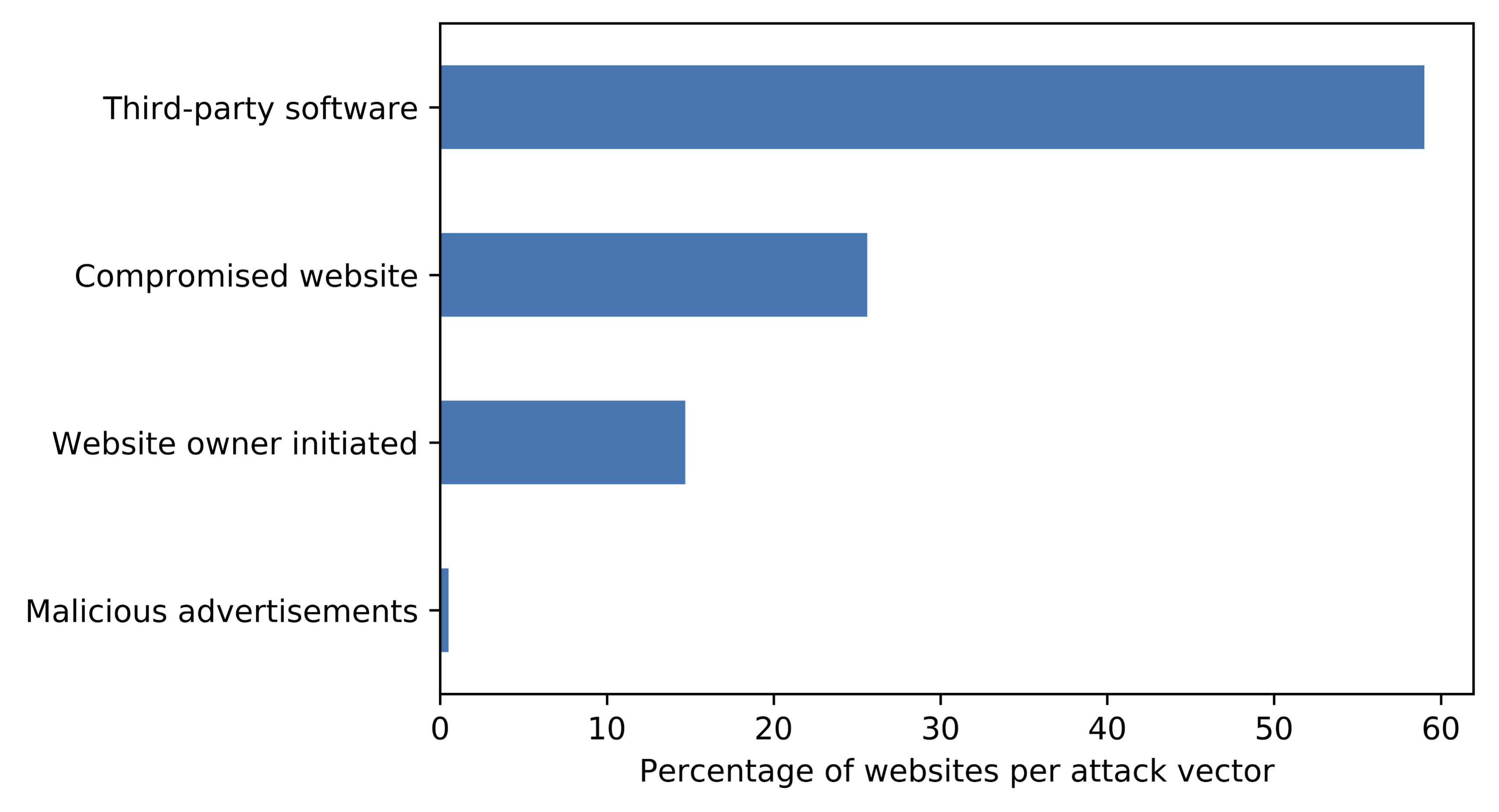
Blog: Infected third-party software key driver for cryptojacking

How not to get milked by the cash cow of cryptojacking

ETL2020-Cryptojacking e BOOK EN- Enisa Amenaza #15 - From January

Reading The ENISA Threat Landscape Report 2018

PacNOG 23: Introduction to Crypto Jacking
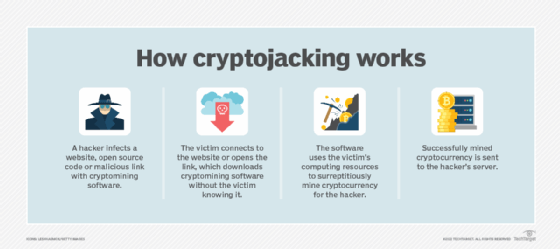
What is Cryptojacking? Detection and Preventions Techniques
Are you seriously using CoinImp?! · Issue #660 · joemccann

PacNOG 23: Introduction to Crypto Jacking

What You Must Know About Cryptojacking in 2022
/images/2022/12/14/what_is_cryptojacking.jpg)
What Is Cryptojacking and How Does It Work?

PacNOG 23: Introduction to Crypto Jacking
Recomendado para você
-
Crypto Miner Blocker22 dezembro 2024
-
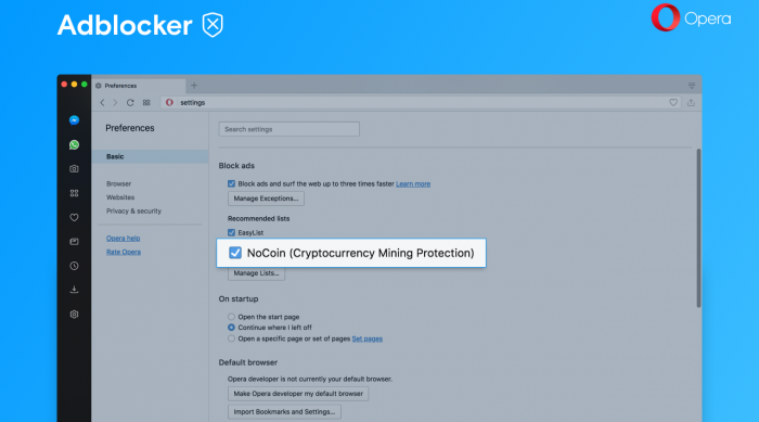 Opera adds anti-cryptocurrency mining feature to mobile browsers22 dezembro 2024
Opera adds anti-cryptocurrency mining feature to mobile browsers22 dezembro 2024 -
 Bitcoin Mining on the Cheap? USB Block Erupter ASIC Miner Review22 dezembro 2024
Bitcoin Mining on the Cheap? USB Block Erupter ASIC Miner Review22 dezembro 2024 -
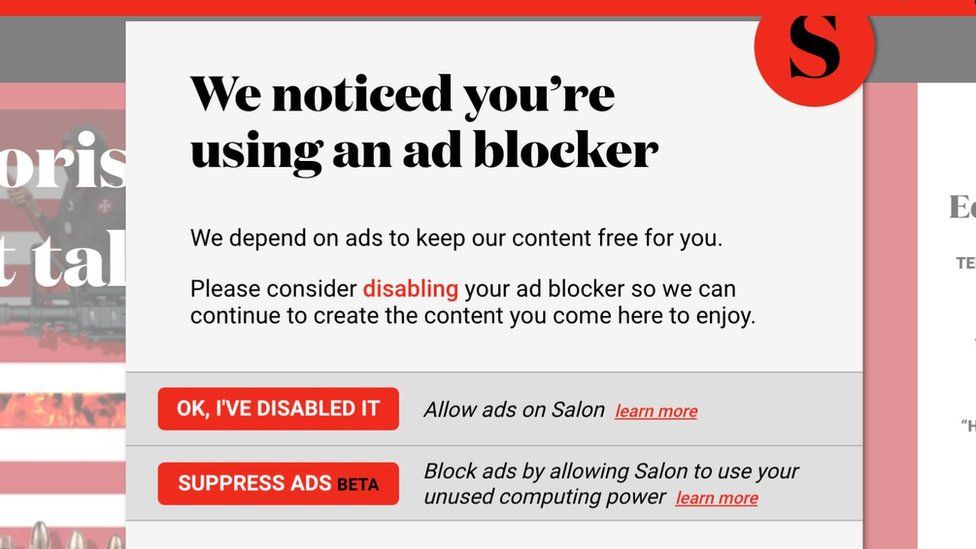 Salon magazine mines crypto-cash with readers' PCs - BBC News22 dezembro 2024
Salon magazine mines crypto-cash with readers' PCs - BBC News22 dezembro 2024 -
 Bitcoin Miners Building Rigs Must Navigate World of Crypto Power-Hunting - Bloomberg22 dezembro 2024
Bitcoin Miners Building Rigs Must Navigate World of Crypto Power-Hunting - Bloomberg22 dezembro 2024 -
 Colorado Avalanche Game Used Pro Stock Bauer Mach Glove and Blocker Miner #122 dezembro 2024
Colorado Avalanche Game Used Pro Stock Bauer Mach Glove and Blocker Miner #122 dezembro 2024 -
 Another Solo Bitcoin Miner Finds Valid Block - Bitcoin Magazine22 dezembro 2024
Another Solo Bitcoin Miner Finds Valid Block - Bitcoin Magazine22 dezembro 2024 -
 Evaluating the Effectiveness of Miner Blocker Browser Extensions22 dezembro 2024
Evaluating the Effectiveness of Miner Blocker Browser Extensions22 dezembro 2024 -
 Cryptocurrency mining affects over 500 million people. And they22 dezembro 2024
Cryptocurrency mining affects over 500 million people. And they22 dezembro 2024 -
 Fake MinerBlock Extension Repeatedly Playing Videos in the22 dezembro 2024
Fake MinerBlock Extension Repeatedly Playing Videos in the22 dezembro 2024
você pode gostar
-
 Sebby memes. Best Collection of funny Sebby pictures on iFunny Brazil22 dezembro 2024
Sebby memes. Best Collection of funny Sebby pictures on iFunny Brazil22 dezembro 2024 -
 IMAGENES TRISTES con FRASES para Whatsapp ◁🥇▷ +100022 dezembro 2024
IMAGENES TRISTES con FRASES para Whatsapp ◁🥇▷ +100022 dezembro 2024 -
 baki ordem manga22 dezembro 2024
baki ordem manga22 dezembro 2024 -
 minecraft sideblog — Pit was a Hell Hunters agent! The hell hunters are22 dezembro 2024
minecraft sideblog — Pit was a Hell Hunters agent! The hell hunters are22 dezembro 2024 -
 Kano 🔥 : r/MortalKombat22 dezembro 2024
Kano 🔥 : r/MortalKombat22 dezembro 2024 -
 Pokemon TCG Tapu Koko GX Rainbow Rare 153/145 Sun & Moon Guardians22 dezembro 2024
Pokemon TCG Tapu Koko GX Rainbow Rare 153/145 Sun & Moon Guardians22 dezembro 2024 -
 Lil Yachty New York Concert Review: Rap and Rock Hits at Central Park22 dezembro 2024
Lil Yachty New York Concert Review: Rap and Rock Hits at Central Park22 dezembro 2024 -
 GRID™ Autosport APK apk+obb 1.6rc9.android - download free apk from APKSum22 dezembro 2024
GRID™ Autosport APK apk+obb 1.6rc9.android - download free apk from APKSum22 dezembro 2024 -
 Garten of banban group all characters! Magnet for Sale by TheBullishRhino22 dezembro 2024
Garten of banban group all characters! Magnet for Sale by TheBullishRhino22 dezembro 2024 -
Roxie Girl anime avatar maker – Apps on Google Play22 dezembro 2024