Anti-Exfil: Stopping Key Exfiltration, by Blockstream, Blockstream Engineering Blog
Por um escritor misterioso
Last updated 19 setembro 2024

In the wake of our recent launch of Blockstream Jade, we’d like to talk about a feature we’ve developed to eliminate the possibility of a certain hypothetical undetectable attack that a hardware…

The Cyber Kill Chain or: how I learned to stop worrying and love
There is a CSS injection vulnerability in the ad blocking
APT Kill chain - Part 2 : Global view - Airbus Defence and Space Cyber

Blog - Block Key Capital - Research
The State of Ransomware: 2020's Catch-22 - Security News - Trend
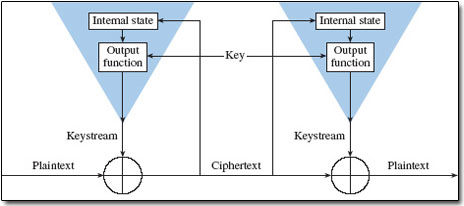
An Overview of Cryptography

Targeted Phishing Attack against Ukrainian Government Expands to

Expanded Blockstream Team To Focus on Bitcoin Scripting And
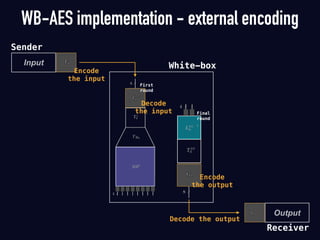
Key recovery attacks against commercial white-box cryptography

Blockstream Users Targeted by Phishing Email

Anti-Exfil: Stopping Key Exfiltration
Clickjacking Attacks and How to Prevent Them
Recomendado para você
-
 Blockstream Jade Pack •19 setembro 2024
Blockstream Jade Pack •19 setembro 2024 -
 Blockstream Jade Review 2023: Pros, Cons And How It Compares - Athena Alpha19 setembro 2024
Blockstream Jade Review 2023: Pros, Cons And How It Compares - Athena Alpha19 setembro 2024 -
 Jade Hardware Wallet Review: Bitcoin Only Wallet19 setembro 2024
Jade Hardware Wallet Review: Bitcoin Only Wallet19 setembro 2024 -
 Blockstream Jade + Billfodl19 setembro 2024
Blockstream Jade + Billfodl19 setembro 2024 -
 Blockstream Jade Now Mines Bitcoin - Just Wait 11 Trillion Years for a Block! : r/Bitcoin19 setembro 2024
Blockstream Jade Now Mines Bitcoin - Just Wait 11 Trillion Years for a Block! : r/Bitcoin19 setembro 2024 -
 Free 3D file Blockstream Jade Cold Wallet Bitcoin Dummy・3D printable model to download・Cults19 setembro 2024
Free 3D file Blockstream Jade Cold Wallet Bitcoin Dummy・3D printable model to download・Cults19 setembro 2024 -
Blockstream on X: Jade is the most secure #Bitcoin hardware wallet available and it's built to last. Visit the #BlockstreamStore to get your hands on a limited edition Jade Transparent to buffer19 setembro 2024
-
 Crypto-Guide on X: Having fun with @Blockstream Jade Bitcoin Hardware wallet. This sets the standard for what Open Source Hardware wallets can look like. Running Jade on TTGO T-display ($10), M5StickC-Plus ($20)19 setembro 2024
Crypto-Guide on X: Having fun with @Blockstream Jade Bitcoin Hardware wallet. This sets the standard for what Open Source Hardware wallets can look like. Running Jade on TTGO T-display ($10), M5StickC-Plus ($20)19 setembro 2024 -
 DIY Bitcoin Hardware Wallet running Blockstream Jade Firmware (Low Cost, Open Source ESP32 Project)19 setembro 2024
DIY Bitcoin Hardware Wallet running Blockstream Jade Firmware (Low Cost, Open Source ESP32 Project)19 setembro 2024 -
 Blockstream Jade & Metal Bundle19 setembro 2024
Blockstream Jade & Metal Bundle19 setembro 2024
você pode gostar
-
 Crazy Time — História, Estatísticas e Resultados19 setembro 2024
Crazy Time — História, Estatísticas e Resultados19 setembro 2024 -
 Nintendo Switch Has Surpassed The Wii's Lifetime Sales In The US19 setembro 2024
Nintendo Switch Has Surpassed The Wii's Lifetime Sales In The US19 setembro 2024 -
 Test (wrestler) - Wikipedia19 setembro 2024
Test (wrestler) - Wikipedia19 setembro 2024 -
 Caixa de Brinquedo com Blocos de Montar 28 Peças - Wp Connect19 setembro 2024
Caixa de Brinquedo com Blocos de Montar 28 Peças - Wp Connect19 setembro 2024 -
 10 Anime Like Bleach You Should Watch - Cultured Vultures19 setembro 2024
10 Anime Like Bleach You Should Watch - Cultured Vultures19 setembro 2024 -
 5 jogos de tiro que rodam em qualquer PC! Baixe agora mesmo, é grátis19 setembro 2024
5 jogos de tiro que rodam em qualquer PC! Baixe agora mesmo, é grátis19 setembro 2024 -
 RS terá seis empresas presentes na maior feira de games da América19 setembro 2024
RS terá seis empresas presentes na maior feira de games da América19 setembro 2024 -
 cult film freak: JAN-MICHAEL VINCENT IN BUSTER AND BILLIE19 setembro 2024
cult film freak: JAN-MICHAEL VINCENT IN BUSTER AND BILLIE19 setembro 2024 -
 DEXSHUN Denji Cosplay Costume Uniform Mask Wig Set Role Play Halloween Anime Carnival Party Outfit Stage Show : Clothing, Shoes & Jewelry19 setembro 2024
DEXSHUN Denji Cosplay Costume Uniform Mask Wig Set Role Play Halloween Anime Carnival Party Outfit Stage Show : Clothing, Shoes & Jewelry19 setembro 2024 -
 Turbo Golf Racing Gears Up For Launch on Game Preview and Xbox Game Pass19 setembro 2024
Turbo Golf Racing Gears Up For Launch on Game Preview and Xbox Game Pass19 setembro 2024
